January 28th is an internationally recognized day dedicated to creating awareness about the importance of privacy and protecting personal information. Industry participants across the world have joined together to create a global community that respects privacy, safeguards data, and enables trust. These same principles apply to the Shared Assessments Program community that is the Trusted Source in Third Party Risk Management.
Privacy regulations have continued to hit the headlines in the past few years with GDPR, CCPA, emerging State Regulations, even updated frameworks from ISO and NIST. It has felt to our members like a bit of “privacy and framework fatigue” to figure out how to update and maintain the right set of privacy-focused controls for third party risk in such a dynamic environment.
To address the needs of its membership and the broader third party risk community, each year the Shared Assessments Third Party Risk Management Toolkit is updated by members for use by members. Due to the expansion of privacy regulations focused on data governance, third party disclosures and tracking of data, an expanded set of Third Party Privacy Tools was updated and released to subscribers in 2020. These tools support and enhance the existing tools for questionnaire development or for performing testing of controls during onsite or virtual assessments.
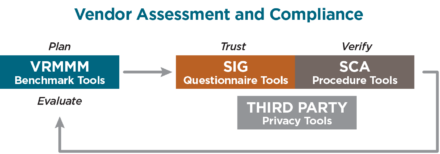
Here’s a snapshot breakdown of what’s included in the Third Party Privacy Tools and a recap of the Best Practices outlined by the Shared Assessment Program Privacy Working Group on how to leverage and optimize these tools for ongoing support of third party privacy risk management.
Whether your organization is an outsourcer who needs to assess the privacy obligations of its’ vendors, or your organization is a service provider that accesses, processes, transfers, or stores personal information, the Third Party Privacy Tools can be used to address both types of privacy obligations.
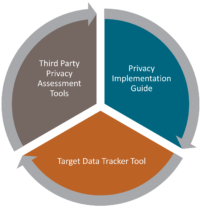
- Educate your Team: The Privacy Implementation Guide provides a Privacy 101 Primer on a review of privacy and critical topics for third party risk that involve privacy data governance. Share this guide with your third party risk analysts to help educate them on privacy controls vs. security controls!
- Identify & Track Privacy Data: The Target Data Tracker Tool streamlines and simplifies the information-gathering process used in third party privacy assessments. Identify and track the privacy classification of data at both third party and fourth party locations.
- Leverage Due Diligence Templates: The Privacy Tools include stand-alone templates that can be used for privacy readiness planning, pre-scoping, data tracking or to support an organizations’ Data Protection Impact Assessment with critical vendors.
5 Ways Shared Assessments Program Subscribers can use the Third Party Privacy Tools:
Managing privacy risk in third party relationships is not a once and done activity – there are ongoing obligations for oversight beyond the planned timeframe for onboarding a new vendor or conducting a cyclical vendor review. Managing privacy compliance and obligations with vendors is an Evergreen process. Here are some of the best practices insights to enhance your internal processes for third party risk.
#1 – UTILIZE THE TDT TOOL WITHIN YOUR DATA GOVERNANCE PROCESS
It all starts with the data. What type of data? Who owns the data? What is the data flow? Managing data governance today is beyond physical and electronic records – it is about the context of the data. The use of the data. The Target Data Tracker Tool can be used as a data collection mechanism to gather information about critical third party relationships as a part of your data map journey to updating data and vendor inventories. The TDT can be used to identify not only the type of data by privacy classification, and type of data subject, but to enhance record-keeping of key attributes on the intended use of the data and the protection of the information.
#2 – INTEGRATE THE TOOLS INTO YOUR DATA PROTECTION IMPACT ASSESSMENT PROCESS (DPIA)
Privacy regulations are increasing the focus on the need to conduct initial and periodic data protection impact assessments. Whether driven by the triggers defined under the GDPR, or other privacy regulations, the assessment starts with a review of any business process involving personal data. Such review is completed with a thorough understanding of the data that is collected, how it is used, what controls are in place, and tracking of disclosures or transfers. The Third Party Privacy Tools can be used as Project Management Templates to assist your organization with defining and structuring a DPIA using standardized templates. These artifacts can be leveraged to enhance compliance documentation to demonstrate the completion of a DPIA that impacts particular business processes that include disclosures to third parties or require third party processing.
#3— USE THE TOOLS TO CONDUCT PRE-ASSESSMENT OR SCOPING OF THIRD PARTY RELATIONSHIPS
All vendors are not alike – just as all risks are not alike. When new Privacy Regulations like CCPA or GDPR are being implemented, it takes planning and a triage process to determine how to prioritize conducting assessments of existing third party relationships to a new set of requirements. The Standardized Privacy Questionnaire provides a set of filtering or scoping questions to identify if a vendor has triggered particular privacy jurisdictions. The TDT enables the collection of information about data use, transfers, and locations to scope third party or onsite assessments. After collection of information gathering using the SIG and the TDT, an organization can re-assess or segment their vendors for a comprehensive privacy assessment.
#4 – PREPARE FOR CHANGE AND USE THE TOOLS IN PRIVACY READINESS ACTIVITIES
When new standards or regulations in the privacy area are being developed and implemented, organizations start with readiness activities prior to building their implementation plans to address compliance. Privacy readiness initiatives require a deeper dive into privacy practices that focus on what functions and data have been outsourced or are processed by third parties. The Privacy 101 Primer provides educational guideposts to key privacy principles, put into the context of what the vendor is doing on your behalf. The complete set of tools can be used for self-assessment or readiness for new privacy obligations in today’s landscape. The assessment topic areas included in the tools can serve as templates to gap analysis activities in the review of your third party risk management program for specific privacy requirements.
#5—LEVERAGE THE TOOLS TO ENABLE YOUR PROCESSES FOR THIRD PARTY INVENTORIES
One of the most challenging processes in Third Party Risk Management is managing the inventory of vendors. While vendor inventories focus on tool automation, contracts, and the governance of the terms of the relationship, the inventory may not have the privacy context needed to focus on third party disclosures. The TDT and its ability to “connect the dots” between third party, use of data, type of data, and location at both third party and Nth Party relationships can simplify your data collection work effort. The TDT can even be proactively maintained by a Service Provider or Data Processor to enhance record-keeping obligations on its points of contact for privacy, breach, or compliance, the record of processing activities, or the authorized use of the personal data. Standardizing the collection effort can simplify the process for staff, while improving the accuracy of data that may be input into software tools for ongoing vendor management.
These highlighted best practices were incorporated into the Target Data Tracker Components graphic to demonstrate both the flexibility and standard approach to using the Third Party Privacy Tools to enhance the privacy risk assessment project management disciplines for both outsourcers and service providers.
Being Privacy Aware is not just about third party risks. Being Privacy Aware is important for employees, for individuals and businesses. For additional information and industry resources on Data Privacy Day, check out the following free resources to use throughout the year when providing Privacy and Security Training!
Update Your Privacy Settings:
https://staysafeonline.org/stay-safe-online/managing-your-privacy/manage-privacy-settings/
Training Tip Sheets and Videos:
https://staysafeonline.org/resources/
The Third Party Privacy Tools are included in the TPRM Toolkit for Program subscribers. The tools can be purchased separately for non-subscribers. Find out about membership subscription levels or contact for general inquiries, email info@santa-fe-group.com.


