Ready or not, IoT third party risk is here. Given the proliferation of connected devices, today’s cyber climate is evolving and organizations have to shift their focus to the security of external parties, now more than ever,” said Charlie Miller, Senior Vice President...
Robin Slade
Fourth Party Risk Management Paper
Jun 3, 2017 | White Papers
Risk from downstream parties is increasing as outsourcing organizations engage more and more third parties who themselves have their own outside provider relationships. The proliferation of fourth party relationships provides the undesired opportunity for the...
Continuous Monitoring of Third Party Vendors: Building Best Practices
Jun 3, 2017 | White Papers
Moving the Needle on Longitudinal Tracking for More Effective Processes Continuous monitoring, a subset of ongoing monitoring, moves the risk posture of systems to a level that allows tracking over time, often in real-time, to raise awareness of changing...
2016 Shared Assessments Benchmark Study
May 5, 2017 | Benchmark Study
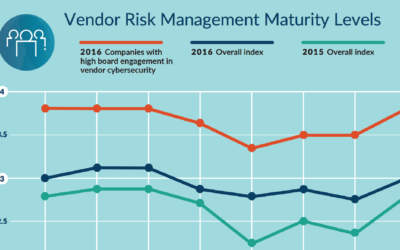
The 2016 Vendor Risk Management Benchmark Study by Shared Assessments in collaboration with global consulting firm Protiviti examines the maturity of vendor risk management.
Building Best Practices in Third Party Risk Management: Involving Procurement Paper
May 3, 2017 | White Papers
Establishing a strong standard for risk management means including all stakeholders before a third party is brought on board. The paper focuses on ways to effectively integrate Procurement into the third party oversight function.
Financial Services Industry Call to Action
Apr 3, 2017 | White Papers
The increased connectivity and complexity of critical infrastructure systems both nationally and globally puts economic and public security squarely at the forefront of risk management in every sector and industry vertical. A proactive stance is clearly required to...
2016 Tone at the Top and Third Party Risk Survey
Dec 5, 2016 | Benchmark Study
Tone at the Top and Third Party Risk examines the role of executives in third party risk management in a broad range of industries and the effect of tone at the top on minimizing business risks within organizations. This study is sponsored by Shared Assessments and...
Sign up for our Newsletter
Learn about upcoming events, special offers from our partners and more.
Sub Topics
- Agreed Upon Procedures (AUP)
- Artificial Intelligence
- Assessment Firms
- Banking and Financial Services
- Benchmark Study
- Best Practices
- Best Practices
- Best Practices
- Big Data
- Board of Directors
- Brexit
- Briefing Paper
- Business Continuity
- Business Resiliency
- California Consumer Privacy Act (CCPA)
- Certification
- Certified Third Party Risk Professional (CTPRP)
- Cloud Computing
- Collaborative Onsite Assessment
- Compliance
- Contracts
- Corporate Culture
- Corporate Reporting
- Cyber Crime
- Cyber Insurance
- Cyber Risk
- Cyberattacks
- Cybersecurity
- Cyberwarfare
- Data
- Data & Cybersecurity
- Data Breach
- Data Governance Tools
- Data Privacy Day
- Data Protection
- Dodd-Frank
- Education and Training
- Environmental Social Governance (ESG)
- Event
- FINRA
- Framework
- Fraud
- General Data Protection Regulation (GDPR)
- Global Risk
- Governance
- Guidance
- Hacking
- Health Insurance Portability and Accountability Act (HIPAA)
- Healthcare
- Incident Reponse
- Industry Members
- Industry Verticals
- Information Security
- Internet of Things (IoT)
- Larry Ponemon
- Licensees
- News
- News And Events
- Office of the Comptroller of the Currency (OCC)
- On-site Assessment
- Operational Risk
- Operational Technology (OT)
- Outsourcing
- Pandemic Planning
- Payments
- Payments
- PCI
- PHI
- Ponemon Institute
- Press Release
- Privacy
- Program Tools
- Program Tools
- Public Policy
- Regulations
- Regulatory Compliance
- Regulatory Requirements
- Research And Publications
- Risk
- Risk Assessment
- Risk Compliance
- Risk Management
- Risk Professionals
- Security
- Service Providers
- Shared Assessments
- Shared Assessments Summit
- Standardized Control Assessment (SCA)
- Standardized Information Gathering (SIG)
- Standards
- Supply Chain
- Supply Chain
- Survey
- Third Party Oversight
- Third Party Risk
- Third Party Risk Management
- Tokenization
- Tone at the Top
- Tools & Templates
- Uncategorized
- Vendor Assessment
- Vendor Oversight
- Vendor Risk
- Vendor Risk Management
- Vendor Risk Management Maturity Model (VRMMM)
- Vendor Security
- Virtual Assessment
- Webinar
- White Papers