California consumers embarked on a new data privacy journey this year by wading through thousands of emails detailing corporate privacy policy updates related to the California Consumer Privacy Act (CCPA) that took effect Jan. 1.
The 500,000 or so companies with customers in the Golden State have a more difficult path to follow, one strewn with CCPA-driven operational changes they’ll need to make to sustain compliance with the new law. Many of those changes center on relationships with third-party vendors.
Data Privacy Day marks an opportunity for data privacy experts and third party risk managers to map out the road they need to travel to satisfy a new data privacy compact between businesses and consumers, as well as between companies and their vendors. The new contract emerged thanks to the 2018 passage of the European Union’s General Data Protection Rule (GDPR), the more recent enactment of CCPA and the pending passage of similar (though, notably, not identical) data privacy rules in at least a dozen other U.S. states. One of the most neglected, yet crucial, aspect of these new rules is that your company’s data privacy hygiene and compliance hinges on your vendors’ data privacy hygiene and compliance.
The pivotal role that vendors’ information security capabilities play in helping to ensure a companies’ information security has been painfully illustrated in recent year through massive data breaches. The 2013 Target breach remains a vivid demonstration of how a cyberattack on a small vendor (an HVAC provider in this case) can infect a large company, resulting in a massive loss of revenue and the sudden departure of C-level executives.
A similar dynamic holds sway regarding data privacy. The infographic below and continued article highlight the considerations managers involved in ensuring internal compliance with CCPA, GDPR and other data privacy rules and standards should keep in mind when addressing third party data privacy risks:
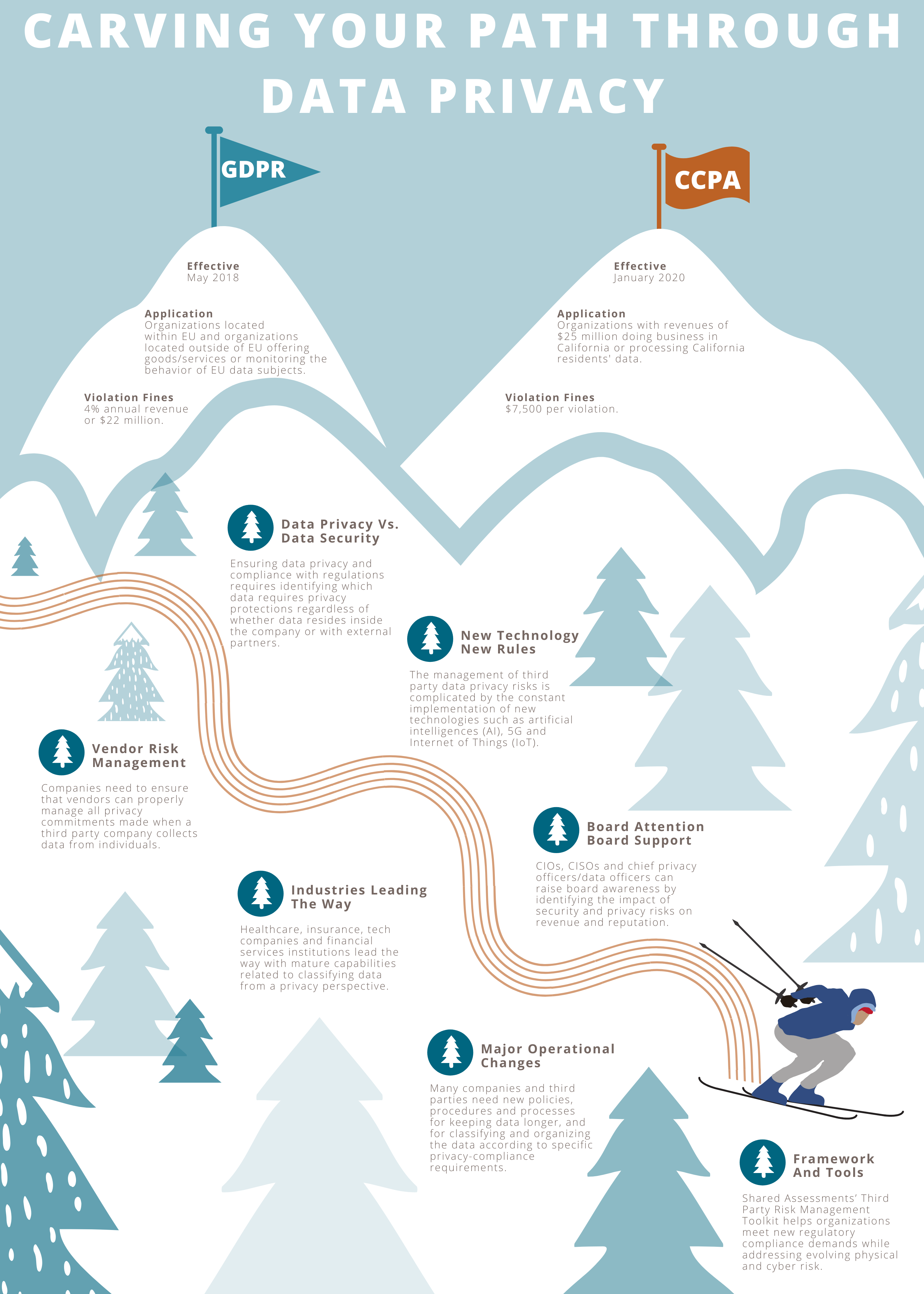
- Data privacy depends on, but differs from, data security: Prior to state, federal and global regulators’ recent focus on data privacy, organizations tended to protect their data from an information technology (IT) security standpoint: Is the data secure, encrypted in transit and stored in a risk-intelligent manner? This mindset remains necessary, but it is no longer enough. Ensuring data privacy and compliance with data-privacy regulations requires internal privacy experts to identify and tag which data requires privacy protections. That inventory of regulated data must be maintained and continuously monitored to ensure that privacy requirements are satisfied, regardless of whether data resides inside the company or with external partners.
- Effective data privacy capabilities hinge on effective third party risk management: Internal information security and data privacy marks a sweeping organizational challenge. Permission and user access controls, employee security awareness, patch management, system configuration management and periodic penetration testing represent a handful of the many activities required to ensure internal data security. In addition to managing data privacy risks and requirements inside the organization, companies also need to ensure that certain vendors can properly manage all the privacy commitments that are made when their company collects data from individuals. In a survey of third party risk management capabilities conducted by The Shared Assessments Program and Protiviti, privacy practices within U.S. companies received the largest portions of “at or above target” maturity evaluations on a 5-point scale — “ fully implemented and operational” (Level 4) or “continuous improvement” (Level 5). That’s good news. The bad news is that only 43 percent of those survey respondents rated their TPRM privacy maturity at or above target; most risk managers rated these capabilities as “ad hoc or no activity.”
- Advanced technologies can cause new data privacy risks: The management of third party data privacy risks is complicated by the constant implementation of new technologies (e.g., artificial intelligences (AI), 5G and Internet of Things (IoT) technologies). IoT technology transmits data through a mix of modern-era software and old-school industrial systems — the latter of which typically lack present-day cybersecurity functionality. The portion of data breaches caused by an unsecured IoT device increase from 15 percent in 2017 to 26 percent in 2019 “and the results might actually be greater because most organizations are not aware of every unsecure IoT device or application in their environment or from third party vendors,” according to the current Third Party Risk for the Internet of Things (IoT) survey report from Ponemon Institute and The Santa Fe Group. Of greater concern: one-third of respondents to the IoT risk survey report that no single person is responsible for the governance of IoT risks inside organizations.
- The new privacy compacts require major operational changes: To meet new data privacy rules, third party risk managers now need to ensure that vendors can properly manage all the privacy commitments that are made when their company collects data from individuals. Fulfilling this new obligation requires major operational changes. Many companies and third parties need new policies, procedures and processes for keeping data longer, and for classifying and organizing the data according to specific privacy-compliance requirements. Companies need to create and maintain an accurate inventory of all regulated data shared with third parties while monitoring how vendors comply with new privacy requirements.
- Data privacy requires board attention and support: While cybersecurity now represents a board-level concern at many, if not most, companies, directors also should be aware of data privacy risks. Chief information officers (CIOs), chief information security officers (CISOs), chief privacy officers and/or chief data officers can raise board awareness by identifying the impact of security and privacy risks on revenue and reputation, providing real-world examples of those negative impacts, and sharing industry benchmarks on cybersecurity and data privacy spending among other steps. boards of directors can do their part by establishing a risk committee; appointing at least one director with C-level data security/privacy experience; meeting at least once annually with the organization’s top IT/cybersecurity/privacy leader; and educating themselves on industry best practices, frameworks and standards related to data protection and third party risk management.
- Some industries lead the way on data privacy: Healthcare and insurance companies, tech companies and financial services institutions lead the way when it comes to third party risk management privacy practices, according to the 2019 Vendor Risk Management Survey Report from Protiviti and Shared Assessments. Companies in these industries have developed more mature capabilities related to classifying data from a privacy perspective; collecting information about data protection controls from vendors’ including provisions in service-level agreements that address how customer data should be managed in a secure, private and compliant manner; and more.
- Frameworks and tools are valuable enablers: Several different frameworks and tools support third party risk management. As third party risk managers strive to convey the need for the additional resources to develop and TPRM program that addresses new data privacy regulations, it is crucial to recognize that the most effective tools continually evolve to keep pace with changing risks and a range of factors that influence third party risks. The 2020 version of Shared Assessments’ continually updated Third Party Risk Management Toolkit helps organizations meet new regulatory compliance demands while addressing evolving physical and cyber risk.
The current Toolkit also features expanded third party privacy tools for GDPR and CCPA. Regardless of which framework and tools an organization deploys to manage third party risks, it is important that those tools reflect current regulations.
Given how many state-level data privacy regulations are currently moving toward finalization — and given the fact that a U.S. version of GDPR at the federal level appears unlikely to materialize during a contentions election year — it’s wise to assume that more and different data privacy requirements are coming down the pike. It’s also safe to say that your company’s compliance with these rules also depends on how well your company manages its vendors’ data privacy risks.


