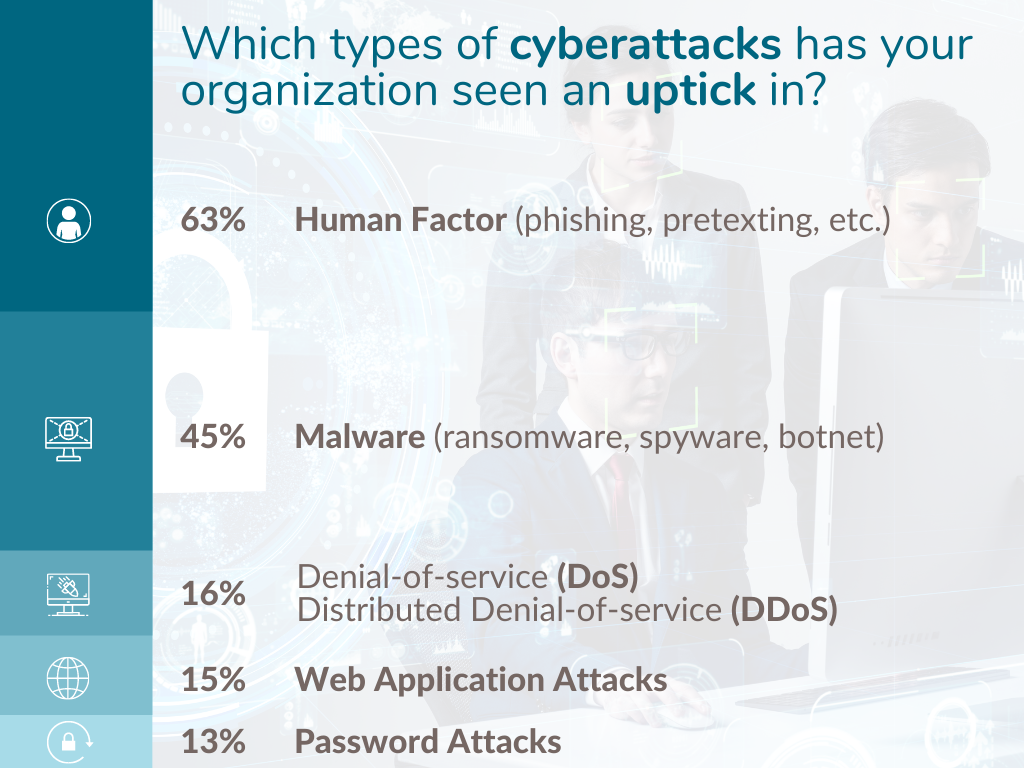
Concern from cybersecurity and third party risk professionals over the risk cyberattacks pose to supply chains is increasing. The Shared Assessments Community reports an uptick in the following types of cyberattacks:
In response to growing anxiety, Nasser Fatah, Senior Advisor, Shared Assessments, and Mike Jackson, Cybersecurity Advisor, Cybersecurity and Infrastructure Security Agency (CISA), presented a webinar that:
- Reviewed notable supply chain attacks
- Defined steps for external dependencies management
- Included a review of supply chain regulations
- Concluded with a lineup of resources to manage supply chain risk
Notable Supply Chain Cyberattacks
In reviewing notable supply chain attacks, the webinar mentioned the 2013 attack on Target’s database resulting in theft of data for over 40 million customers via an HVAC vendor. Another notorious attack was the 2017 exploit of a known vulnerability in software code running on Equifax web servers, resulting in theft of Personal Identifiable Information (PII)of 147 million Americans.
The webinar touched on two quotes that show just why vendor risk management is the antidote to supply chain attacks:
- “The weak link in your enterprise security might lie with partners and suppliers…” Maria Korolov. CSOOnline. January 25, 2019.
- “50% of today’s attacks leverage ‘island hopping’…” 2019 Global Incident Response Threat Report. Carbon Black.
External Dependency Risk
External dependency risks are risks that arise in relying on external entities to support an organization’s critical services.
Examples of external dependencies include cloud services involving third party processing of information, infrastructure dependencies such as electricity and transportation, and governmental dependencies including emergency response to support data centers.
Additionally, technology providers, vendors, suppliers are all external dependencies.
Critical Services
Identifying critical services helps to focus external dependencies management. Critical services fall under four categories: people, information, technology, and facilities.
- People ‒ Those who operate and monitor the service
- Information ‒ Data associated with the service
- Technology ‒ Systems that automate and support the service
- Facilities ‒ Where the service is performed
Steps For External Dependencies Management
To manage the risks introduced by dependencies on external entities, external dependencies management is key. Steps to this approach include:
1. Identify services based on criticality to the organization.
2. Identify and map external dependencies (map the dependency to the services they support).
3. Protect and sustain operations by evaluating external dependencies, risk, resilience requirements, service level agreements, control objectives.
4. Establish continuity requirements for operations that rely on external dependencies
5. Conduct Cyber exercises to gauge the strength of your External Dependencies Management Strategy
Notable Supply Chain Laws and Directives
In recent years, these supply chain regulations are of note:
- Secure and Trusted Communications Networks Act of 2019
- Secure 5G and Beyond Act of 2020
- 2018 SECURE Technology Act
- Federal Acquisition Supply Chain Security Act
- HIPAA Omnibus Rule
- Cybersecurity Maturity Model Certification (CMMC)
Resources For Supply Chain Cyberattacks and Risk Management:
- DHS National Risk Management Center
- CISA Supply Chain Risk Management Task Force
- Securing the Information and Communications Technology and Services Supply Chain (Trump’s Executive Order 13873)
Additionally, an External Dependencies Management Assessment can further the efficacy of managing risks in the supply chain.



