You wouldn’t leave your home without making sure the door was shut and locked behind you. You wouldn’t install an alarm system that doesn’t sound when a burglar enters. So, why would you not take the same precautions for your company? Consistently testing the effectiveness of application security controls is crucial in protecting your organization and mitigating risk.
Most modern organizations rely heavily on numerous third parties within their supply chains to keep their business running and successful. Some businesses, however, may lack the processes and skills to best understand how their supply chain and third parties can pose additional risk. With a clear understanding of potential risks to the supply chain, organizations can take advantage of strategies and application security controls to mitigate harm.
In our recent Innovations In Third Party Risk Processes: Application Security Controls webinar, Managing Partner at Radical Security, Paul Poh, and Director of TPRM Professional Services at Echelon Risk + Cyber, Tom Garrubba, discuss various Third Party Risk innovations designed to approach common security pitfalls. Poh and Garrubba explore how application security best practices can mitigate risks for company networks, systems, and data.
What are the minimum or baseline controls to look for when conducting testing?
When conducting testing on vendors, the priority is to make sure your third-party libraries, or open-source libraries, do not have vulnerabilities. There are baseline security controls that can be done to accomplish this goal. These controls include vulnerability scanning (should be done prior to pen testing), dependency checking, dynamic and static code analysis, and general quality assurance (QA) testing. Threat modeling is another integral technique used in software development and the testing process. Every time a major change occurs, systematically identifying and rating the threats that could be introduced by such changes, will help defend the security posture of an application or computer system. These minimum controls highlight a better understanding of whether an end user’s behavior is going to introduce weaknesses in the application itself.
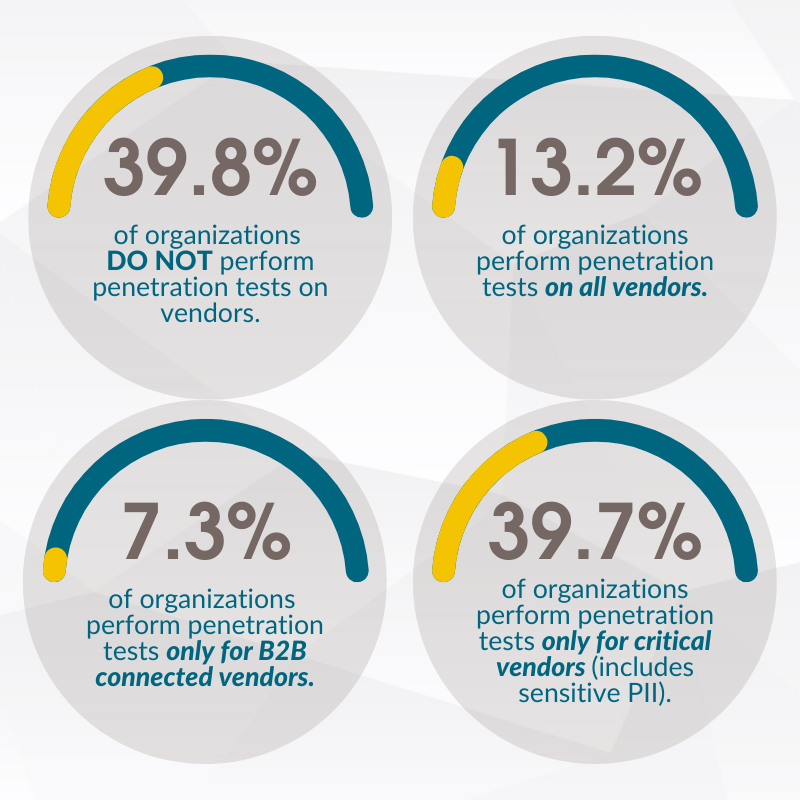
What is penetration testing and why is it important?
Penetration testing, also referred to as “pen testing,” is an authorized cyberattack on a computer system to identify and expose vulnerabilities and weaknesses within an organization’s security posture, potentially gaining access to features and data. Pen testers will mimic the strategies and actions of a hacker to evaluate a system’s hackability and address any possible issues.
Application Pen Testers bring value to the third-party risk assessment process. Penetration testing is a crucial security technique to ensure that your organization understands its system and the potential risks it may pose.
A few important things for assessors to keep in mind regarding application penetration tests:
• First, ensure that the test being conducted is not an automated test. There are certain types of vulnerabilities that cannot be found through an automated means, thus, requiring a human who understands how applications are created to perform the test.
• Whether the test is performed internally or externally, understand the qualifications of the pen tester and/or team and whether they are qualified to perform the test.
• Know what to look for in a report and understand what the report contains.
• Be sure to ask for the unredacted report from the pen tester. If you receive the executive summary, make sure it was created by the pen tester. Reports should include the scope, the duration of findings and how many as well as the qualifications of the testers.

Is Penetration Testing Considered a Secure Systems Development Life Cycle (SDLC)?
In short, pen testing is not a secure SDLC. A secure SDLC implies that the development process itself, from ideation to change management, actual coding, quality assurance (QA), and deployment, has security at each tollgate. Ideally, vendors will be using frameworks for their software development that are well vetted and well known to ensure that they get input sanitization and are using gems for authentication that are common. Organizations should view security and secure SDLC frameworks as a competitive advantage. A secure framework adds value to the customers you service. When you talk to vendors, you can assess if security is important to them by asking what kind of security measures or testing they employ.
Key Takeaways/Checklist
• When evaluating pen test reports, pay attention to the qualification of the analyst that performed the testing.
• Penetration testing is not the same activity as vulnerability scanning.
• Basic Application Security hygiene should include dependency vulnerability scanning.
• Understand how vendor application authentication works.
• A vendor’s application development stack can provide insight into vendor secure coding processes.
Conclusion
As technology and innovation continue to evolve, organizations must know and understand the potential risks posed to their company by cyber criminals. For companies to successfully protect against attacks and breaches, they need to be able to enact application security measures and best practices. By doing so, organizations can quickly identify, update, and improve parts of their system that are susceptible to harm.


