This week, the White House National Security Council has organized a virtual Counter-Ransomware Initiative meeting. The purpose of this meeting is to strengthen President Biden’s leadership in gathering allies and partners to neutralize a common threat: ransomware. The ministers and representatives from more than 30 countries “recognize that ransomware is an escalating global security threat with serious economic and security consequences.”
Notably, Russia and China were both excluded from the list of invitees due to “various constraints.” Nevertheless, this does not mean that both countries will be excluded from attending further meetings on ransomware. (In June, President Biden and Russian President Vladimir Putin put their efforts into creating a working group in which both countries could connect on ransomware.)
“Any time nations can come together to collaborate on tactics and techniques to disrupt the ransomware ecosystem is a welcomed endeavor. This is an increasingly pressing issue in turbulent times as organizations and even nations appear to tire of becoming hostage to cyber terrorists. The time is ripe for a global coalition to address what would hopefully be a “zero tolerance” policy towards the safe harboring of such threat actors and bring about swift and decisive justice to curtail such future acts. One could only hope,” says Tom Garrubba, Vice President, Shared Assessments.
The main objectives of the Counter-Ransomware Initiative meeting are for G7 leaders to understand the importance of the international community assisting one another in the resiliency of critical infrastructures against cyber-attacks, investigating and prosecuting those who are involved with malicious cyber activity, notating the cyber-attacks occurring within their respective borders, and reinforcing cyber defenses.
Biden Administration’s Ransomware Strategy
The Biden Administration’s strategy to combat ransomware centers around 4 efforts: disruption, resiliency, currency, and diplomacy. The infographic below details U.S. efforts to counter ransomware.
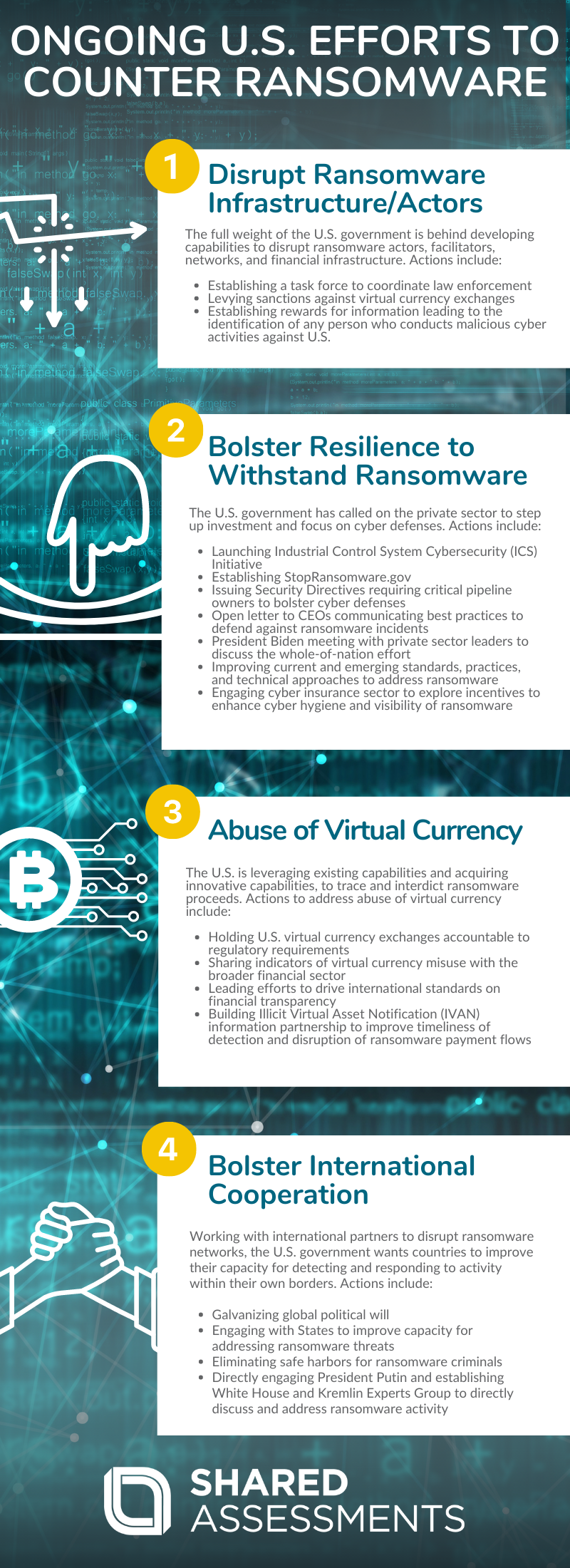
Disrupt Ransomware Infrastructure and Actors
To Disrupt Ransomware Infrastructure and Actors the full weight of the U.S. government is being applied to develop capabilities to disrupt ransomware actors, facilitators, networks, and financial infrastructure. Actions to date include:
- Department of Justice (DOJ) establishing a task force to coordinate and align law enforcement and prosecutorial initiatives combating ransomware.
- Treasury holding money laundering networks accountable. The Treasury has levied its first-ever sanctions against a virtual currency exchange.
- US Cyber Command and National Security Agency dedicating resources to generate insights and options against ransomware actors.
- Department of State’s establishing a reward of $10 million for information leading to the identification of any person who engages in, aids or abets, malicious cyber activities against the U.S.
Bolster Resilience to Withstand Ransomware Attacks
To Bolster Resilience to Withstand Ransomware Attacks the Administration has called on the private sector to step up its investment and focus on cyber defenses to meet the threat. Actions on the resilience front to date include:
- Launching an Industrial Control System Cybersecurity (ICS) Initiative – a voluntary, collaborative effort between the federal government and the critical infrastructure community.
- Establishing the StopRansomware.gov website to help organizations access resources to mitigate their ransomware risk.
- Transportation Security Administration (TSA) at the Department of Homeland Security issuing two Security Directives, requiring critical pipeline owners and operators to bolster their cyber defenses.
- Deputy National Security Advisor for Cyber and Emerging Technology, Anne Neuberger, sending an open letter to CEOs communicating best practices to defend against and prepare for ransomware incidents.
- President Biden meeting with the private sector and education leaders to discuss the whole-of-nation effort needed to address cybersecurity threats.
- National Institute of Standards and Technology (NIST) working with industry to improve current and emerging standards, practices, and technical approaches to address ransomware.
- Treasury and the Department of Homeland Security’s CISA are engaging the cyber insurance sector to explore incentives to enhance implementation of cyber hygiene and improve visibility of ransomware activity.
Address the Abuse of Virtual Currency to Launder Ransom Payments
To Address the Abuse of Virtual Currency to Launder Ransom Payments virtual currency is subject to the same Anti-Money Laundering and Countering the Financing of Terrorism (AML/CFT) controls that are applied to fiat currency, and those controls and laws must be enforced. The Administration is leveraging existing capabilities and acquiring innovative capabilities, to trace and interdict ransomware proceeds. Actions to address the abuse of virtual currency include:
- Continuing to hold U.S. virtual currency exchanges accountable to our regulatory requirements, and sharing indicators and typologies of virtual currency misuse with the broader financial sector.
- Treasury leading efforts to drive implementation of international standards on financial transparency related to virtual assets to build bilateral partnerships designed to strengthen controls for virtual currency exchanges overseas.
- Led by the Federal Bureau of Investigation, building an Illicit Virtual Asset Notification (IVAN) information sharing partnership to improve the timeliness of detection and disruption of ransomware payment flows.
Ransomware incidents have increased with the invention of cryptocurrency. Ron Bradley, Vice President of Shared Assessments reflects that “Before there were banks, there were no bank robbers. Before cryptocurrency, ransomware was barely a blip on the radar screen. The anonymity of cryptocurrency allows for threat actors to operate indiscriminately, and much more broadly than if they had to walk into a bank with a gun for a stickup. While it’s true some progress has been made to recover ransomware payments, there is still a very long way to go in order to stem the tide.”
Bolster International Cooperation
To Bolster International Cooperation the U.S. is working with international partners to disrupt ransomware networks and improve partner capacity for detecting and responding to such activity within their own borders, including imposing consequences and holding accountable those states that allow criminals to operate from within their jurisdictions. Actions to date to bolster international cooperation include:
- Working closely with international partners to address the shared threat of ransomware and galvanize global political will to counter ransomware activities.
- Continuing to engage with States to improve their capacity for addressing ransomware threats.
- Eliminating safe harbors for ransomware criminals through a more direct diplomatic approach. (President Biden has directly engaged President Putin, and established the White House and Kremlin Experts Group to directly discuss and address ransomware activity.)
Actions TPRM Can Take Against Ransomware
A firmer understanding of the U.S. government’s approach to combatting ransomware, what should third party risk management do to withstand ransomware attacks?
“Cybersecurity resiliency has been on the radar screen for regulators for some time, and rightfully so because we need to anticipate cyberattacks – either opportunistic or targeted. When a cyberattack like ransomware transpires, it not only quickly tests the resiliency of one’s cybersecurity program, but also the resiliency of an organization because of the impact ransomware has on an organization. It is important for organizations to prevent ransomware, but just as essential for an organization to timely detect and respond (know what to do in the event of an incident) to ransomware. To identify it, contain it, and eradicate it in a timely manner, otherwise, one will be learning crisis management during a crisis,” shares Nasser Fattah, Senior Advisor, Shared Assessments.
Charlie Miller, Senior Advisor, Shared Assessments suggests that “organizations should exercise ransomware cyber event scenarios with their critical suppliers to ensure all areas of their organizations are prepared and can respond to a ransomware attack.”
Miller identifies the main components as:
- Identifying key individuals from multiple departments and ensure executive management participation in cyber exercise realistic and varied scenarios to ensure, timely and corrective actions are clearly understood and executed.
- Ensuring you have law enforcement contacts identified and participate in your exercises.
- Having retainer agreements in place for key technical resources to have those resources at the ready to assist in the response.
- Availability of a current hard copy playbook for use by internal and critical vendor incident response teams is at the forefront of ensuring a realistic enterprise-wide incident response.
- Regularly testing to ensure the incident team is able to manage, coordinate, and respond appropriately before, during, and after the attack.
Additional information on ransomware and cybersecurity:
- Blogpost: Cybersecurity Awareness: The Suspense Is Killing Us!
- Blogpost: How To Be Cyber Smart – 5 Must Knows
- Blogpost: Workplace Safety, Security, and Data Governance




