Establishing a Third Party Vulnerability Campaign – Webinar Overview

In the wake of the Solarwinds attack, Tom Garrubba, Vice President and CISO, Shared Assessments led an expert panel discussion on establishing third party vulnerability campaigns. Speakers included:
- Frank Roppelt – Senior Manager, Security Policy and Vendor Risk at TD Ameritrade
- Rocco Grillo, Managing Director – Global Cyber Risk & Incident Response Investigation Services, Alvarez & Marshal
- Daniel Cuthbert, Global Head of Cyber Security Research, Banco Santander
Garrubba directed the dialogue towards three areas of focus. First, panelists defined a vulnerability campaign. Next, the group touched on how vulnerability campaigns help companies prepare for the next attack. Finally, the experts examined how to gain assurance that a third party has addressed a vulnerability. I. Defining a “vendor vulnerability campaign” – what does it do and why do it? Frank Roppelt defined a vendor vulnerability campaign as an effort to develop a deep understanding of how susceptible your third parties are to vulnerabilities and what the corresponding impact would be on your organization. Rocco Grillo characterized a campaign as an overall threat hunting effort with a comprehensive approach. Daniel Cuthbert, having spent the last 20 years on the offense against threats, profiled attackers as having high confidence and an eye “on the soft belly” that is our network of vendors. In a vendor vulnerability campaign, the focus must shift from securing the front door (of your business) to assuring security across the organizations that keep our business running (the outliers, the suppliers, the support services). II. Understanding how a vendor vulnerability campaign can help prepare a company for the next widespread vulnerability Acknowledging the supply chain as a prominent form of business, Grillo said technology is sure to evolve, as will attacks and the regulatory landscape. Lean into the concept of “trust, but verify.” Roppelt described third parties as extensions of your ecosystem: extremely beneficial, but not without risk. In addition to normal due-diligence, it is important to have a process outlined that is ready to be executed at a moment’s notice. Preparation includes building your program with a designated tiger team and identifying the vendors that are your most critical and high risk. Cuthbert assured that when dealing with vendors it is ok to be demanding. It is reasonable to expect that when you buy a product, you can ask is your product secure? Companies need to be demanding, get proof of a secure platform, and secure development practices. When vendors are hesitant to give these answer, it is a red flag. III. Gaining assurance that a third party has addressed a vulnerability Garrubba asked if there is a certain documentation or test to guarantee a third party has addressed for vulnerabilities. All panelists agreed assurance is not a check-the-box exercise and offered specific processes and questions for third party risk programs to protect against vulnerabilities inherited from vendors. Frank Roppelt submitted actions for developing a Risk Culture Approach to apply prior, during and after a third party vulnerability is discovered. 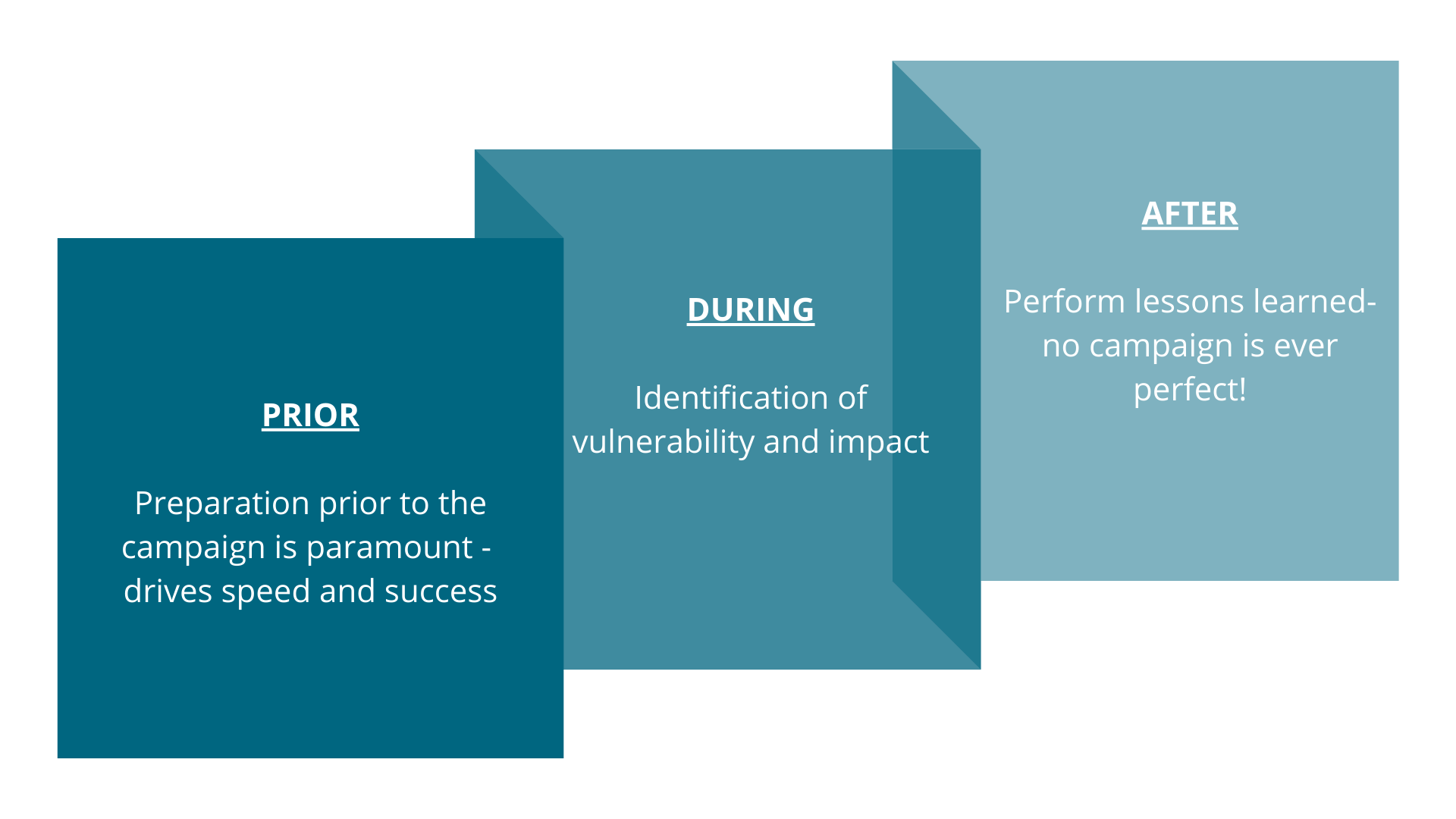 Prior
Prior
- Preparation prior to the campaign is paramount -will drive speed and success
- Maintain listing of high risk and critical third parties who H,P, T, S sensitive information and verify the contact is still accurate. Preferably a cyber contact and not a sales rep
- Partner with network team to understand what third parties/partners have connectivity to your network
- Understand what third parties are hosting internet facing solutions that ultimately lead to your data
During
- Identification of vulnerability and impact
- Determine the risk of exploit and the impact this will have on your firm via a supply chain attack
- Select which vendors must be part of the campaign and execute vendor with specific questions
- Enact tiger team to run campaign (does not need to be a fulltime role), daily huddles for status and escalation
- Report status to leadership on response rate, number of affected vendors, areas of concern
- Determine course of action based on risk identified and remediate to acceptable level
- Dig in –If needed, pull in business lines, get on the phone, possibly enact legal to get clarity of remediation or initial response
- If vendor is unresponsive after all attempts, create findings and escalate to senior leadership
After
- Perform lessons learned -no campaign is ever perfect! Determine pros and cons and perform next steps to be better
- Prepare for next campaign
Rocco Grillo suggested the audience ask themselves these questions as they develop their approach to third party vulnerabilities:
- What actions and steps have CISOs and their security teams taken in response to the cyber-attacks that we have witnessed over the last 12+ months?
- Given the state of cyberattacks on third party services providers, CISOs and cyber teams need to become more diligent than ever regarding their organizations’ supply-chain controls. What do companies need to be doing now?
- How should companies be communicating both the short-and long-term impact regarding third party service provider attacks to company CEO’s and Board’s?
Cuthbert reiterated his stance that understanding is vital – and that third party risk programs should demand more of it from critical vendors by demanding to see:
- SDLC policies
- Proof of shifting left in their continuous integration and continuous deployment (CI/CD) pipelines
- Roadmap of fixing the issues
For a full recording of this webinar and the slide deck, visit our webinar archive page.
Feedback Agreement
By downloading this software, you acknowledge that you may be invited to provide usability feedback to help improve its functionality. Feedback does not guarantee changes or compensation.

