Nth Party Suppliers – Gaining a Toehold on Down Chain Providers

Supply chain sovereignty depends on a high degree of visibility into Nth Party Suppliers in order to identify critical dependencies and then apply a consistent set of principles for monitoring of parallel (redundant) processes and other elements required for resilience across both inbound and outbound supply chains. How to accomplish this remains a nagging question at the practitioner level. As third party and supply chain risks converge, increased demands are falling on outsourcers as well as providers.
Due diligence information gathering must include processes for Nth parties. Typically, practitioners report that they cannot reach far enough into the chain beyond the primary vendor (and their hosted provider) to gain insight into the down chain providers. Yet, outsourcers have to gain a clear understanding of the interdependencies posed by down chain parties so that related risks can be assessed and managed.
Not only is this level of understanding mandated by robust risk management, regulations have begun to emerge globally that dictate outsourcers know, manage, and report on their fourth and Nth parties. Most organizations do not have this big picture view in focus. They are not aware of the risks posed by their Nth parties, nor are they in a position to understand the changes in Nth parties as they occur. As the pandemic has laid bare, this stance is not sustainable.
Identifying critical dependencies
To identify critical dependencies, the complete supply chain needs to be mapped. To conduct a complete risk analysis across your supply chain requires a targeted information management effort that covers both inbound (supplying the outsourcer’s product) and outbound (to the customer) supply chains. Completing this process allows your organization to adopt a proactive stance in which resilience planning can be taken before disruption occurs.
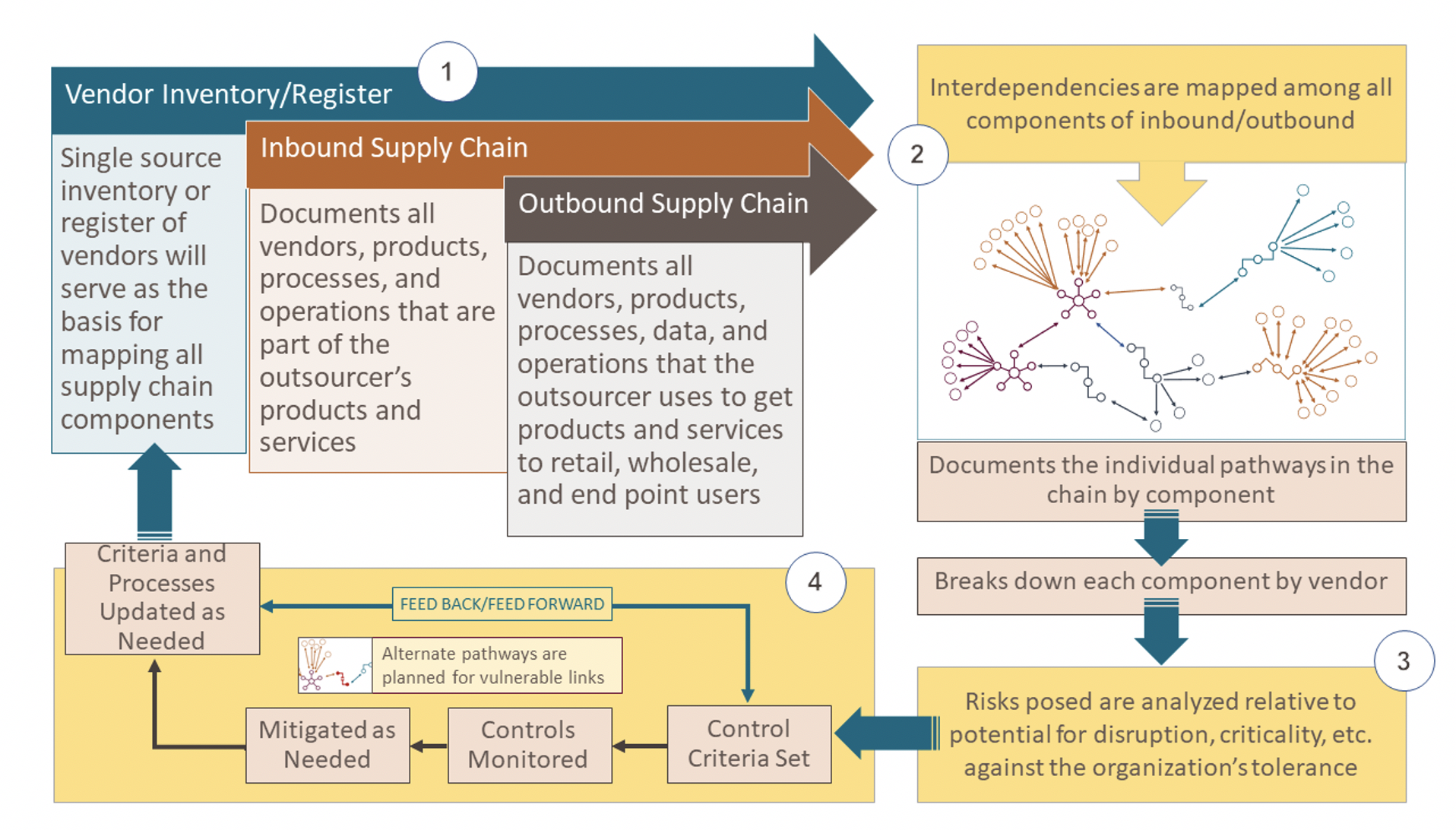
This is not a one-size-fits-all process. TPRM resources are often focused primarily on documenting controls for individual vendors and analyzing the risks posed by those relationships. It is important to qualify what is “material” for the outsourcing organization, so that focus and resources are placed on those risks that are truly material. When supported by strong leadership and robust resources, the TPRM function can collaborate enterprise-wide and across the planning and vendor relationship lifecycle to achieve a more robust information gathering, analysis, and collaboration process.
Key challenges that need to be considered are:
- Noise in the System, which can result from lack of clarity around context and the number of vendors in the chain.
- Lack of Visibility and Transparency, which is are required to follow the components of the chain (data, materials, etc.) and achieve proactive analysis and risk management.
- Scope Creep, where a risk goes unrecognized due to the change in scope of work with a vendor or the concentration risk posed by more business units utilizing the same vendors.
- Skill and Expertise Gaps, are a high risk management failure point where TPRM and supply chain risk management converge.
The combined impact of these challenges can result in being out of sync with the outsourcing organization’s own risk tolerance. Issues include privacy, to unapproved access to systems, and to availability issues. Flow needs to be examined across each aspect of the chain (components, transportation, assembly, III/robots floor manufacturing). Where possible, vendors that manage proprietary information transfer (schematics, other IP) and their downstream providers must be identified as material.
Proactively improving your supply chain risk management
As practitioners grapple with the reactive stance that pervades the risk management community, they can consider the following as means of building a more proactive posture.
- Understand Context. It is critical to scope and assess each vendor based on a real-world, enterprise-wide view of how that vendor interacts with your organization. This requires the participation of business units across the enterprise, and the ability to share assessment results and other vendor information across departments as needed to maintain and understanding context as supply chains shift and vendors change.
- Capitalize on existing resilience planning. Make a point of getting to know your organization’s internal and external resilience processes so that you can maximize their use – and not duplicate efforts. Business continuity plans are a good place to start. Look at key links in the supply chain and determine – ahead of any event – what alternate pathways have been identified. Find out if backup suppliers have been vetted. This may not be feasible in markets where resilience is less important than the cost of this proposition.
- Refresh vendor expectations. Pre-existing contract terms can limit visibility into Nth party relationships and their management by your third parties. For any relationship, inherited or otherwise, when current and emerging risk management requirements need to change, that change needs to be mirrored within the assessment process.
- Push for industry-wide solutions. Advocate with industry peers to push for regulation and advocate for industry-wide solutions to the challenges surrounding Nth party awareness and the need for transparency. Possible scenarios that can be exercised to achieve a useful shift in uncomplicating and protecting supply chains include reshoring (to a more favorable setting) and/or bringing tasks back in-house.
- Pay attention to your vendor intelligence. The vendor intelligence, including continuous monitoring, conducted has to match your organization’s risk appetite and tolerance. Mapping and monitoring is essential at the down chain level. Carefully determine why you need to do a down chain assessment, so that you can gain insight into the areas that are most important for resilience.
- Pay attention to your business intelligence. As with vendor intelligence, you must achieve an understanding of the project goals of business units and how those relate to their vendors and the broad variety of risks being managed.
- Address skill set gaps. Push for education and soft skills development across your organization and ensure that your third/fourth/and Nth parties have the right skills to mitigate risk. Inexperienced risk assessors may provide results that are determined to be less than optimal.
A daisy chain of vulnerabilities and opportunities for strengthening the ecosystem exists in every supply chain ecosystem. Lurking among these networks of suppliers are undefined risks (e.g., the unknowns of the Nth parties). Gaining a holistic view and a tangible grasp of the viability, measurable scope, and practical impacts of the use of Nth parties has to be a goal of robust TPRM. Without it, material fourth/Nth parties can wreak havoc. The presence of this type of undefined risk is simply untenable and does not support a proactive risk management stance.
Regulations are emerging that support the right to audit/access as a right of outsourcers, even when that type of leverage would otherwise would have not existed within the outsourcer/vendor relationship. By conducting assessments that are based on a holistic view of your entire supply chain ecosystem, all the potential uses, transfer points, and other key links can be monitored more effectively. Risk can be normalized earlier in the relationship, and managed with an eye for toward greater resilience.
Since the circular nature of supply chains impacts delivery and availability, all the way down the line, taking a proactive stance now will provide many opportunities, including being ready to respond to regulatory changes that are beginning to reverberate across industries. While this is a significant culture shift for many organizations, its impact on risk management can be profound and entirely worthwhile as your organization begins to improve its visibility to identify critical dependencies and apply a consistent set of principles for monitoring and mitigating risk.
For related practitioner resources, you can download the Nth Party Governance briefing paper here.



