Top 5 Emerging Third Party Risk Threats

Last week, Tom Garrubba, VP, Shared Assessments and Alastair Parr, SVP of Global Products & Delivery, Prevalent, presented the Top 5 Emerging Third Party Risk Threats. The pair offered an overview of:
- Effective remote assessment methodologies
- Proactive event management
- Supply chain resilience to improve assurance
- Stronger third-party situational awareness
- Defining and map key controls to ensure vendors stay on track
1. Effective Remote Assessment Methodologies
Virtual assessments provide efficient and cost-effective evaluation of third party’s controls, reviewing the same controls as onsite assessments. While the pandemic increased the instances of virtual assessments, they have been successfully conducted since 2003.
A remote assessment or virtual assessment is a common approach for lower risk third party service providers. In this type of assessment, a third party completes a questionnaire designed to provide information about how they develop and maintain protection of information assets. This type of assessment hinges on trust as third party “self-assesses” on risk controls.
An onsite assessment is a physical or in person assessment of third party’s risk controls and environment reserved for critical service providers. Onsite assessments look beyond existence of controls testing – they ensure controls are as represented and seek to understanding how a third party executes those controls.
As a TPRM program defines its requirements for virtual collaboration, they will want to consider the various workflows feeding assessments. This can be visualized as a funnel – weighing remediation credits against risk, considering total number of third parties subject to continuous monitoring, understanding risk remediation, assessments, contextual reporting, validation audits, onsite audits, and ad-hoc critical events requiring support.
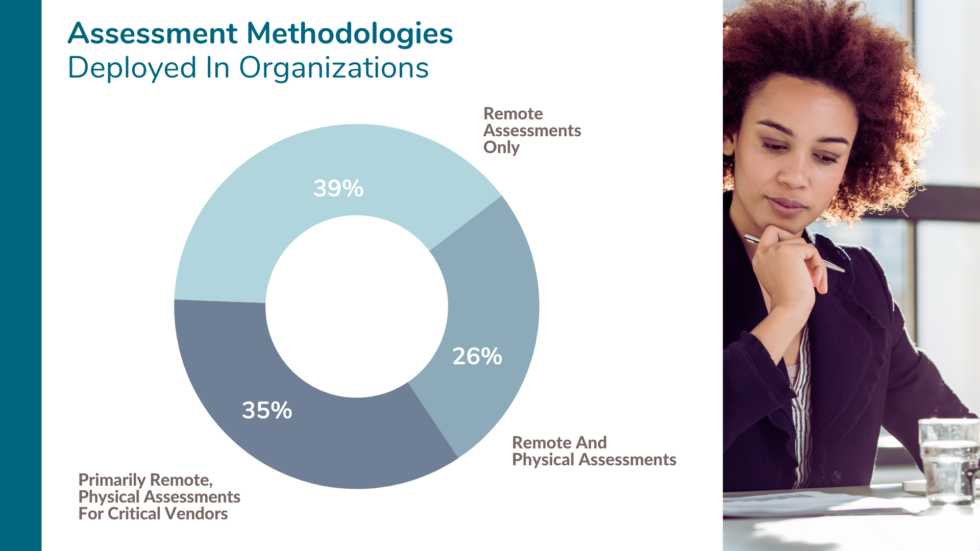
During the webinar, Shared Assessments asked attendees to identify the assessment methodologies their organizations are deploying. Majority of poll takers said they are conducting remote assessments exclusively:
2. Proactive Event Management
Proactive Event Management includes managing for both third party risks and internal risks. To be prepared for security incidents, you need to be aware of coverage factors, ownership factors, visibility and improvement factors. Typical event management workflow moves an organization from unprepared to resilient, going through the phases of record, respond, and recover.
Resiliency “requires focus in multiple areas when integrating Business Continuity and Disaster Recovery approaches into an overall Business Continuity Management Program.”
Shared Assessments asked webinar attendees what event management techniques their organizations use to head off security incidents. The majority use a combination of all techniques: 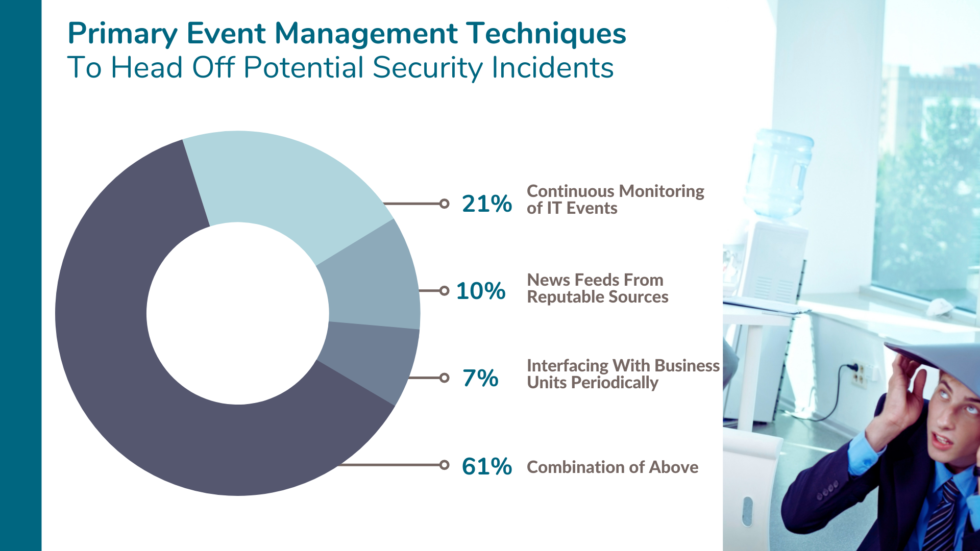
3. Supply Chain Resilience
A Business Impact Analysis (BIA) helps to identify the critical processes and associated systems and prioritizes the effect of a business disruption based on impact and likelihood. A BIA will help you understanding availability, which belies the importance of your vendor services to your organization.
4. Developing Stronger Third Party Situational Awareness
The key to stronger third party situational awareness is constant and open dialogue. Your organization needs to understand a vendor’s current plan and the trends they are following.
What is the business unit’s present and future strategy for outsourcing? As for compliance, what critical topics are on the radar? Is “anticipatory compliance” being practiced?
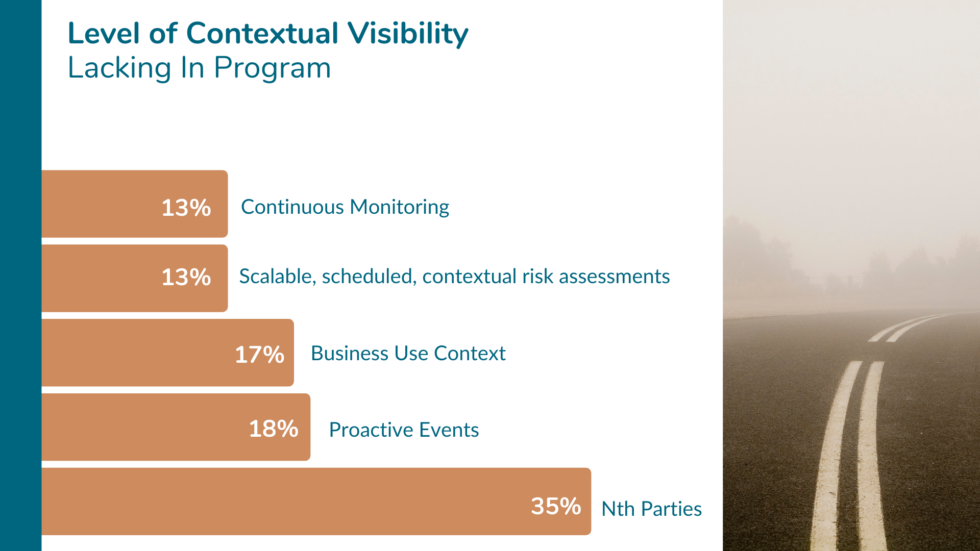
When asked about contextual visibility in TPRM programs, webinar attendees point to Nth Party Risk lacking:
5. Defining and Mapping Key Controls
To identify and address compliance risk, there are increasing risk assessment frameworks and standards with which every risk assessor should be familiar:
- Technical specifications
- Configuration standards
- Risk quantification methodologies
- Demonstrate external assurance to controls
- Ability to achieve external certification
- Self-regulatory assessments
- Shared methodologies
- Defined and formalized control requirements
- Measurable maturity levels
- Benchmarking
- Model governance
- Standardized deployment models
Specific industry sectors require additional guidance, obligations, contractual terms, and control requirements based on nature of each type of product or service offering. Considerations in this realm include:
- Payments compliance
- Prudential banking regulators
- Trade Associations and Member Orgs
- Formalized audits or examinations
- Transactional reporting
- Audit controls
- Quality assurance
- Research requirements
- Consumer protection
- Complaint and dispute handling
- External Certifications
To view the webinar and download the accompanying presentation deck, navigate here.

