Building A Robust Third Party Risk Management Program

Strong third party risk management is a growing requirement in the face of globalization and the increasing dependence on third parties that support core products and functions. Third party risk management (TPRM) revolves around the whole relationship lifecycle. This intricate lifecycle requires organizations to apply an integrated approach that expands the need for robust governance, efficiency and business models that respond to economic pressures that arise from the need to use outside expertise and speed-to-market innovation.
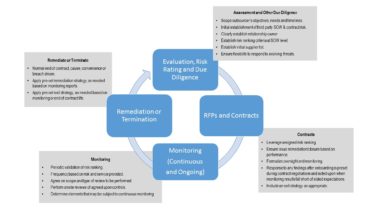
Key elements for a solid third party risk management program involve effective design, communication, control and monitoring of policies and processes, third party and system inventories, contracts, risk tiering and assessment techniques, ongoing oversight, tools and technology and awareness of the threat, regulatory and industry landscapes.
Policies should be guided by C-Suite and Board level input and written for the individual enterprise landscape. Policies must address the complexity of the business relationships and identify key controls. Setting third party foundational requirements that are aligned with relevant organizational goals, as well as relevant regulatory guidance and industry best practices will help define your organization’s risk appetite. Consistent processes and messaging are imperative for good functioning of your governance model and for longitudinal evaluation of the effectiveness of your program. Good planning at this level will also lead to higher compliance levels, due to an increased understanding of the requirements and goals that all stakeholders need to meet.
Procurement, purchasing and sourcing are all critical players in both development and ongoing program success. Involvement of these departments/teams from the start of planning and vendor sourcing will allow your organization to:
- Become increasingly nimble and therefore support innovation and speed to market; and
- Be more consistent by applying predetermined risk criteria to all third party relationships throughout the third party relationship lifecycle.
For inventories, reach out to all your business units and corporate functions that have knowledge of or access to third parties dealing with your organization. This may include, but should not be limited to, key business units, procurement, vendor management and finance. Often finance will have the most complete list, as they may capture third parties who fly under the purchasing/procurement radar.
Completeness is the key to a good inventory and the inventory must be maintained to ensure that regular, accurate updates and reporting are available to stakeholders within the organization. While shrinking your supplier inventory can be efficient and result in cost savings, it can also expose an organization to potential concentration risk.
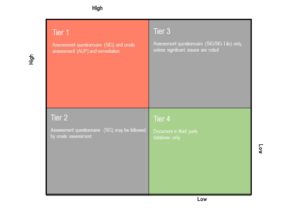
Pre-selection due diligence activities should include a process to rank potential third party suppliers based on consistent risk criteria. Those criteria are generally based on the risk posed to the outsourcing organization relative to the type of services and exposure of data unique to a given third party’s role with your organization. High ranked (Tier 1) third parties would receive a higher level of initial and ongoing control assessments than lower ranked (Tier 2 through Tier 4) third parties.
Identifying key technologies and classification of data involved is at the heart of a strong tiering system. For instance, Personally Identifiable Information (PII), Protected Health Information (PHI), Card Holder Data (CHD) and Confidential, Intellectual Property and Sensitive (CIPS) data that are touched by your third parties would trigger high risk tiering and therefore a deeper level of assessment. The scope and frequency of assessments must be thoroughly addressed and should be based on the third party risk rating ranking within your organization’s standard corporate requirements.
Risk tiering considerations are unique to third party risk and also have product/service inherent risks.
Unique Third Party Risks
- Financial – difficulties and/or failures.
- Strategic – not aligned with business objectives.
- Reputation – impact to brand and your reputation.
- Country – located in a sanctioned country.
- Credit – inability to make obligated payments.
- Quality – inability to deliver product/service in line with specs.
Product/Service Inherent Risks
-
-
- Cyber – confidentiality, integrity, availability of information/technology assets.
- Compliance/legal/intellectual property – inconsistent actions and non-alignment with standards and frameworks.
- Contractual – failure to meet contractual obligations.
- Operational – failures resulting in impacts to operations.
- Resiliency – inability to continue to provide.
-
Contract terms and conditions typically include standard clauses that take into account, including, but not limited to: price, escrow and payment schedules; confidentiality and intellectual property; service level agreements (SLAs); information security; incident response and notification; audit rights; disaster recovery; notification and approval for fourth party change and/or use; cyber insurance; termination/exit strategy; maintenance and assessment types and schedules; complaint handling; cross-border transfers and privacy. Ensure that remediation for any mitigating circumstances are tracked, resolved within agreed upon time periods and well-documented. Schedule onsite reviews, as appropriate to the global setting and regulatory climate.
A clear determination should be made during negotiations, in writing, as to the period over which assessments are to be made and/or if what types of events are considered assessment triggers. The type of assessment should also be agreed upon, such as the Shared Assessments Standard Information Gathering (SIG) Questionnaire and Shared Assessments Agreed Upon Procedures (AUP).
As part of due diligence, risk rating and contract development must take into account the eligibility of that third party and assessment of the controls relative to the product or service that will be provided.
Ongoing oversight is part of a holistic program with point in time assessments being the most common historically. There is a fast growing trend toward continuous monitoring, which is advancing along with the technology required for ongoing, transparent scoring of key indicators for third parties. Using a third party risk software solution to evaluate and score third party risk both for initial due diligence and for ongoing monitoring and incorporating those results into your Enterprise Risk Management (ERM) solutions is a way to leverage technology to achieve a more robust and effective TRPM program.
TOP 10 TPRM CONSIDERATIONS:
-
-
- Sponsorship and governance that has full Board and C-Level support.
- Scope that is clearly defined in breadth and depth.
- Complete, regularly updated inventory of third parties, contracts, systems, data, control assessments, etc.
- Policy that includes specified risk criteria and alignment of control policies with all parties – business units, information security, physical security, business resiliency/disaster recovery, human resources, privacy, compliance, third party and operational risk management.
- Process for pre-selection, contract, ongoing oversight, termination, embedded risk metrics.
- Technology and tools that are crisp, functional, and designed for quick adaptation to a changing threat landscape.
- Reporting that provides tracking, risk monitoring, scorecards, etc.
- Skills and expertise that is clearly defined, qualified, certified and disciplined.
- Education that provides employees, procurement and third parties with clear, consistent information and messaging.
- A high level of regulatory requirement and industry best practices standards awareness, including Shared Assessments, AICPA, Cloud Security Alliance, and Payments Card Industry (PCI).
-
In summary, leverage technology solutions, support end-to-end processes and documentation, identify critical records and integrate your solutions with business unit goals. Work to ensure that your staff and assessors are trained at appropriate levels and have defined roles and responsibilities. Work to develop, capture and report key metrics. And train third parties in policy awareness and regulatory requirements that are specific to your relationship.
By involving business and sourcing units enterprise-wide in your program design and implementation, you can achieve a more adaptive and easy-to-use program that will serve both your employees and your providers. Stakeholders span the organization, from the Board of Directors and C-Level executives, to business units, purchasing, human resources, control groups and technology.
Charlie Miller, is a Senior Vice President with The Santa Fe Group, Shared Assessments Program, with key responsibilities that include managing and expanding the Collaborative Onsite Assessments Program and facilitating regulatory, partner and association relationships. Charlie was previously the Director of Vendor and Business Partner Risk Management at AIG, where he managed regulatory and governance activities for the organization’s enterprise vendor risk management program.

