Request For Comments – Interagency Guidance for Third Party Risk Management

Three of the four federal banking regulators have launched an extremely important effort to refresh and harmonize third party risk management guidance for financial institutions in the United States (the comment period closes on September 17th). Shared Assessments plans to respond to the request for comments, and members are invited to participate in the effort – please email Jessica Calzada with your interest.
I’d like to examine three issues sure to be part of the comment barrage, but I would like to do so through an unusual lens. Because so many financial institutions operate across international boundaries, I believe it’s important that updated federal guidance be developed in the context of rapidly evolving global third party risk management standards. So, what follows is a bit of a deep dive in several areas.
The current joint effort by regulators resents a unique opportunity to consider three areas where guidance could smooth cross-jurisdiction pain points:
- Diverging fourth (and Nth) party risk management expectations
- CSP due diligence expectations given the sharply expanded use of cloud services
- Different regulatory approaches to understanding sector-specific concentration risk and resulting divergent inventory (register) expectations for individual firms.
Fourth and Nth Party
Regulators are increasingly focused on the emergence of more complex supply chains and the potential security gaps they create. A November 2020 Financial Stability Board (FSB) report on third party risk documented surprisingly long financial services chains, with participants reaching into double digits (Page 24). While supervisory authorities clearly understand heightened fourth and Nth party risks, international regulatory guidance in some areas seems to be diverging.
Regulators from the EU, Singapore, the UK and the US are consistent in their guidance that outsourcers include contract language requiring service providers to obtain prior approval before engaging fourth parties and/or allow outsourcers to terminate contracts when subcontracting takes place without consent. They also agree that third parties should make subcontractors contractually liable to comply with the outsourcer’s security standards. The notion of a “contractually mandated security hygiene chain” to ensure that outsourcer standards prevail in complex outsourcing arrangements seems firmly established.
While there is general regulatory agreement about appropriate Nth party contract language, there is less coherence around due diligence obligations. On one hand, the Monetary Authority of Singapore requires that outsourcer contracts allow outsourcers (or their agents) to conduct audits on fourth or Nth parties (page 21). On the other hand, more recent European Banking Authority (EBA) and Prudential Regulatory Authority (PRA) guidance place the sole burden for fourth or Nth party oversight on service providers (page 46). In fact, the PRA states plainly (page 30) that “The PRA does not expect firms to monitor fourth or fifth parties.”
In the United States, some Shared Assessments members financial institutions report considerable regulatory pressure during exams for direct monitoring of fourth and Nth parties.
Perspective: U.S. regulators should examine the issue of outsourcer fourth and Nth party due diligence obligations carefully and consult with peer agencies abroad as they craft final language. Deliberations should carefully consider evolving continuous monitoring capabilities and other approaches to improving due diligence in complex outsourcing chains.
Cloud Services Due Diligence
Regulators have clearly received the message from mid and smaller sized financial services organizations that – when dealing with cloud services and other large suppliers – their contractual negotiating power and ability to secure what would otherwise be standard access and audit rights is very heavily constrained. Regulatory reaction to that reality, however, has been inconsistent. 2017 EBA Cloud guidance, subsequently incorporated into the EBA’s February 2019 third party guidance, explains the regulator’s thinking (see table below):
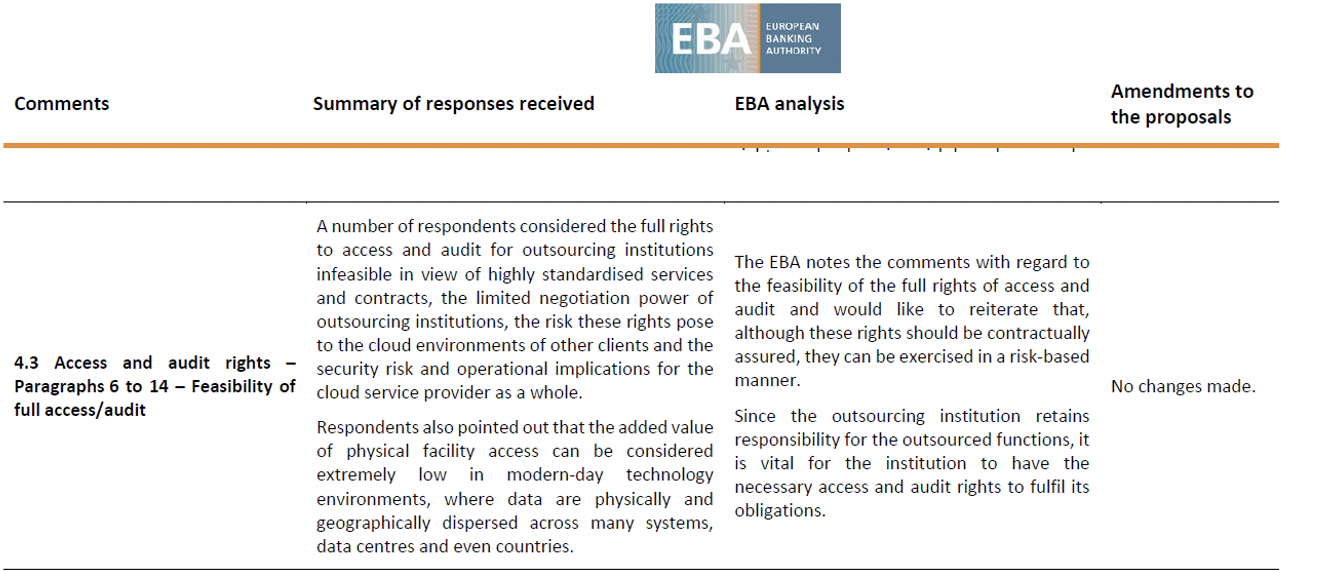
In the US, the interagency consultation document contains updated 2020 language that clarifies the OCC’s current expectations, which seem to mirror the EBA’s:
Third-party risk management for cloud computing services is fundamentally the same as for other third-party relationships. The level of due diligence and oversight should be commensurate with the risk associated with the activity or data using cloud computing… Regardless of the division of control responsibilities between the cloud service provider and the bank, the bank is ultimately responsible for the effectiveness of the control environment. (Question 3)
However, even when regulatory language is consistent (e.g. EU and UK) supervisory authorities are more explicitly demonstrating flexibility about how audit and access language is interpreted. In recent (March 2021) guidance, the UK’s PRA Supervisory Statement SS2/21) includes valuable context about the realities of limited access rights and the type of flexibility the PRA will provide in situations, such as with Cloud Service Providers (CSPs), where onsite audits create undo risk for the service provider:
The SS acknowledges that certain types of onsite audit create may an unmanageable risk for the environment of the provider and/or another client of the same provider, for instance by impacting the provider’s service levels or the confidentiality, integrity, and availability of data. In such cases, the firm and the service provider should agree on alternative ways to provide an equivalent level of assurance. This could, for example, be achieved through the inclusion of specific controls to be tested in a report or certification. The PRA expects that firms should retain their underlying right to conduct an onsite audit. For material outsourcing arrangements, the PRA expects firms to inform their supervisor if alternative means of assurance have been agreed. (PS7/21, page 27)
Perspective: The type of flexibility the Bank of England suggests might be stated more explicitly in the upcoming U.S. Interagency TPRM guidance, especially since U.S. financial services regulators regularly assess cloud service providers and others supporting key industry functions (that authority stems from 12 U.S. Code 1867 – Regulation and Examination of Bank Service Companies), a tool many peer regulators around the world lack.
Sector Specific Concentration Risk
Regulators around the world have been paying more attention to concentration risks that may have serious consequences for the financial services sector. Once mundane third party inventories (registers) have taken on new importance as a result. For example, Monetary Authority of Singapore (MAS) regulations require FI’s to maintain and provide up to 25 columns of detailed data on all outsourcing arrangements. The EBA also requires firms to keep detailed data but ups the ante in terms of how that data should be prepared for collection:
Institutions…should, upon request, make available to the competent authority either the full register of all existing outsourcing arrangements or sections specified thereof…[and] should provide this information in a processable electronic form (e.g. a commonly used database format, comma separated values). (EBA, Paragraph 56, page 38)
The Bank of England made headline third party risk management news in March when it announced its intention to study the development of an online inventory (register) portal for the UK financial services institutions it supervises.
The PRA is planning a follow-up consultation setting out detailed proposals for an online portal that all firms would need to populate with certain information on their outsourcing and third party arrangements, or a subset thereof, such as those deemed material (as noted above). This consultation will take into account the comments provided by respondents to CP30/19 on the idea of developing an online portal. (PS7/21, page 5).
Whether or not the portal becomes a reality, the proposal demonstrates the depth of regulatory concern over the consequences of an attack to take down individual providers critical to the functioning of the UK’s financial sector as a whole.
Perspective: U.S. regulatory language in this area has not been updated, perhaps because federal agencies have access to customer lists through their audits of cloud service providers and other major third party providers. That said, increased international harmonization of inventory (register) requirements would be a welcome product to emerge from the coming regulatory convergence efforts in the United States.
Summary
Concentration risk, fourth (Nth) party risk and access and audit rights are just three issues sure to draw feedback during the comment period. Third party risk practitioners should help inform this “generational” feedback opportunity for the Federal Reserve, FDIC and OCC consultation. Take advantage of the Shared Assessments comment opportunity – email Jessica Calzada add your voice.

