OWASP Top 10: Open Web Application Security Project
Open Web Application Security Project® (OWASP) is a nonprofit foundation that works to improve the security of software. Every year, OWASP releases a “Top Ten” List. The OWASP Top Ten is an awareness document for developers around web application security. The list represents a broad consensus about the most critical security risks facing web applications. It serves as a baseline for compliance, education, and vendor tools.
Why Should I Care About the OWASP Top 10?
Every year, companies should adopt the updated Top Ten list and continue the process of ensuring that their web applications minimize the risks cited on the list. The value of OWASP comes from its checklist of which security risks web application developers should prioritize and how to prevent those risks from manifesting. Using the OWASP Top 10 is perhaps the most effective first step towards changing the software development culture within your organization into one that produces more secure code.
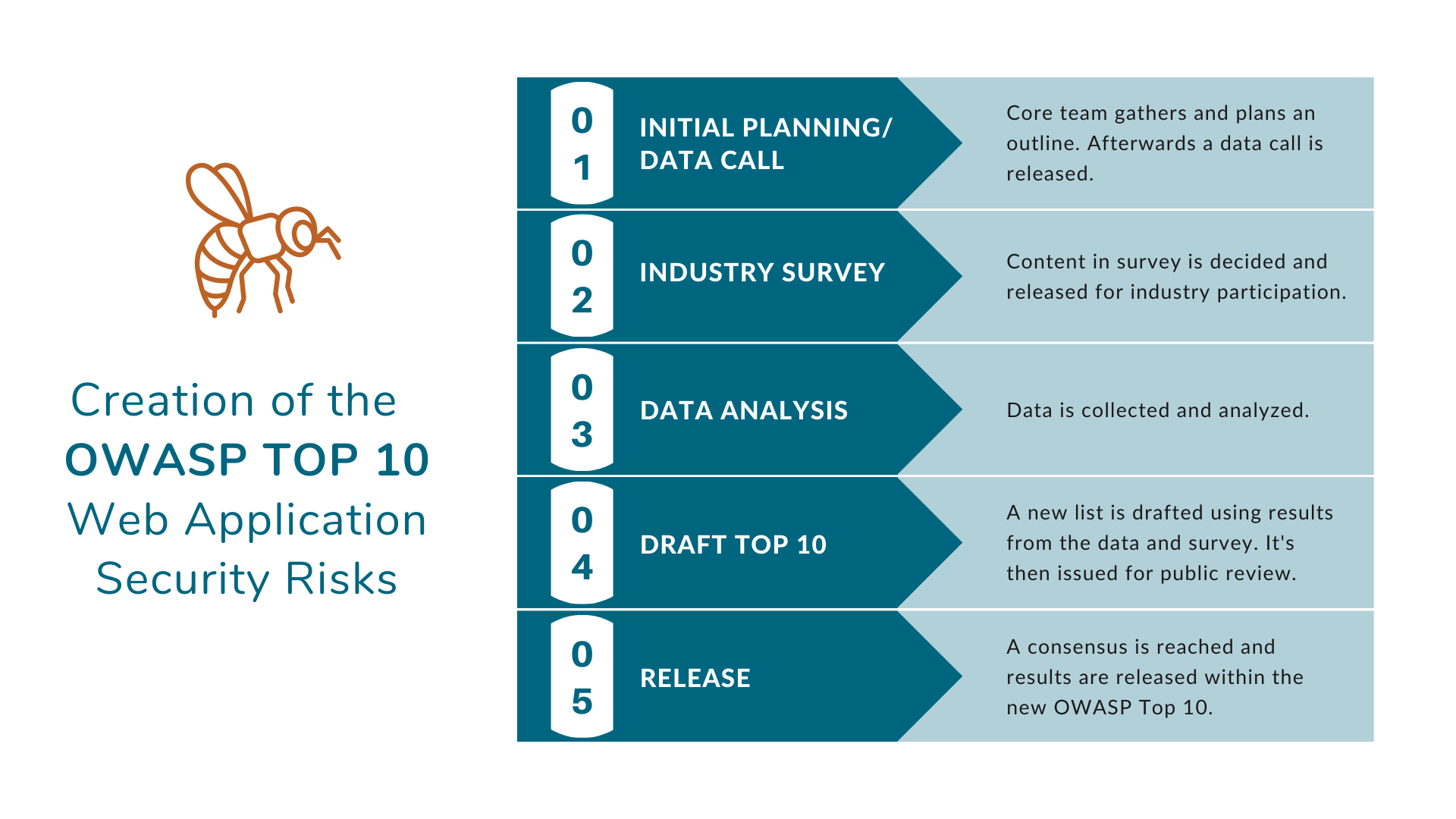
How is the OWASP Top 10 List Created?
OWASP Top Ten List
Last week, the OWASP Top Ten list for 2021 was released. Here are the results:
1. Broken Access Control
Broken access control is when an attacker gains access and control of a user’s accounts. This can lead to unauthorized information being disclosed, modifications, or eradication of data.
2. Cryptographic Failures
This risk occurs when there is vulnerability of sensitive data such as passwords, credit card numbers, health records, personal information, and business secrets that require extra protection.
3. Injection
Injection codes are implemented when an attacker submits invalid data onto a user’s web application which leads to the improper usage of the design.
4. Insecure Design
Insecure design is when there is a lack of design security and privacy-related controls.
5. Security Misconfiguration
Security misconfigurations are design flaws showcasing sensitive data.
6. Vulnerable and Outdated Components
When your platform, framework, and dependency are not updated or upgraded to the latest version it is more susceptible to exploitations from attackers.
7. Identification and Authentication Failures
When an application does not have a weak password check, multi-factor authentication, or session timeout feature.
8. Software and Data Integrity Failures
Software and data integrity failures occur when the coding or infrastructure of an application doesn’t protect against integrity violations.
9. Security Logging and Monitoring Failures
Logging and monitoring are critical and vital to help detect active breaches.
10. Server-Side Request Forgery (SSRF)
Although there is a firewall, VPN, or another type of network access control list in place attackers are able to manipulate a request on an application to obtain a remote resource.
OWASP Top Ten Impact on Risk Management
In response to this year’s changes to the OWASP Top Ten, Shared Assessments’ Vice President, Tom Garrubba, emphasizes that “It’s always interesting to follow the positional swings of existing risks – along with new additions to this list – of the most critical risks in web application security as surveyed by the OWASP community. Since the last updated OWASP Top 10 list, ‘Broken Access Control’ (i.e., giving a user access to different resources and features, or to keep a user away from control) has leaped four places to the number one spot which may be a harbinger of the growth of threat actors gaining access to critical IT resources and features that a typical user normally would not have exposure or even access to. Additionally, having ‘Insecure Design’ being added – and rifling to the number four spot – highlights the need for better web application code design, development, testing and hygiene to addressing web application vulnerabilities.”
Data Contributors
AppSec Labs, Cobalt.io, Contrast Security, GitLab, HackerOne, HCL Technologies, Micro Focus, PenTest-Tools, Probely, Sqreen, Veracode, WhiteHat (NTT), along with anonymous donors shared data for over 500,000 applications to comprise this security data set.
Get Involved
Efforts have been made in numerous languages to translate the OWASP Top 10 List. If you are interested in helping, please contact OWASP (owasp-topten@lists.owasp.org) and mention the language for which you are interested in contributing a translation.

