SOC it 2 Me … One More Time

It’s that assurance time of year again as organizations are kicking into the implementation of their 2018 external audit engagements. We are now under the six-month timeline for new SOC standards to be in place. This is the third year in a row I’ve written about changes in external audit reporting standards that impact service provider controls and executing external assurance engagements. Each year the changes drive maturity, transparency and stronger governance into the process, but also create confusion and need for knowledge. So, let’s dust off the boxing gloves and understand the new assessment protocols that will be in place once we jump back into the audit boxing ring.
Acronyms, Terminology & Methodology – Alphabet Soup
Heavyweight sports fans know terms like Knockout (KO), Clinch. Down & Out. Fall Through the Ropes. Sucker Punch. Throw in the Towel. Prizefighter auditors and assurance practitioners understand terms like AICPA, Attestation. SOC, SSAE18, TSC, CSOC, Carve-outs. Subservice organizations. Qualified Opinion. Information security and IT professionals rely on frameworks like COSO, NIST, and COBIT.
While the terms are quite different the work effort to simply navigate audit standard changes easily creates emotional comparisons to a few of those boxing terms, especially for the non-accountant. Let’s level set on a few of the key concepts that are changing within SOC engagements, but from a more sports fan or business user point of view.
The American Institute of Certified Public Accountants (AICPA) is the national professional organization that sets ethical standards for the profession and U.S. auditing standards for audits of private companies, non-profits, and governments. They have updated their standards and protocols for audit engagements to align with the 2013 Committee of Sponsoring Organizations (COSO) framework which was designed to assess the design, implementation, and maintenance of internal controls and assess their effectiveness. COSO frameworks are traditionally part of the SOX compliance program for financial accounting of public companies.
The changes in the SOC audit reporting will be effective for audit periods ending on or after December 15th, 2018 . That means the changes will be effective for all engagements in 2019, triggering readiness, migration, and process changes in 2018. During this transition, for audit engagements executed in 2018, a company can choose to early adopt the new criteria structure or continue with the current Trust Services Principles.
Report Changes and Updated Naming Conventions
The methodology standards set out in the SSAE18 framework will now apply to all SOC2/SOC3 reports. Those changes include the requirements to clarify control ownership when there are subcontractors or sub-service organizations in scope for the system being assessed. With the remapping effort to the COSO framework, additional terminology changes for SOC audit reports have been defined:
- SOC: Was Service & Organizational Control and now is System & Organizational Control.
- SSAE: Statements on Standards for Attestation Engagements.
- TSPC and TSC: Trust Services Principles & Criteria (TSPC) are being renamed Trust Services Criteria(TSC)
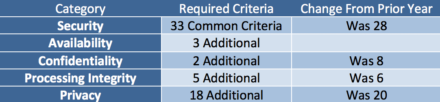
- Principles & Categories: Principles will now be called categories, but they still focus on security, availability, processing integrity, confidentiality, and privacy of a system.
- Risks/Controls: Within the report structure and protocol, the assessor will now use terminology of “points of focus” for the specific control topic area being reviewed.
A SOC2 report must include the Security Category, with all the Common Criteria, and may include the additional categories. Each category will have their own unique criteria to be met as part of the audit. These changes expanded the number of common control criteria and streamlined some of the additional criteria in the Trust Services Categories.
Implications for Service Providers
External assurance audit reports are a mechanism to provide independent assurance and testing of controls. Each service provider defines the type of audit engagement needed to meet their client contractual obligations based on the systems and services that are outsourced. With the growing focus on cyber security and enterprise risk management, many of the changes in common controls have broadened beyond traditional IT controls or public company financial controls. The shift to include risk management functions and programs will trigger the need for additional control owners, compliance documentation, processes to be tested, and includes operational risk management programs.
There are eight new common criteria related to the alignment with COSO principles:
- Board oversight
- Use of information to support internal control
- Sufficiency and clarity of the entity’s objectives
- Identification and assessment of changes
- Controls deployed through formal policies and procedures
- Procedures to identify new vulnerabilities
- Business disruption risk mitigation
- Vendor and business risk management
Third party risk management functions may be implicated in many of these criteria but the focus on Vendor and Business Risk Management as a common control in scope for all engagements shows the growing attention to third party risk. The inclusion will provide a deeper dive into the third-party risk management program structure, implementation, governance and risk reporting. The third-party risk management program elements that will be assessed, audited, and tested include:
- Requirements for Vendor and Business Partner Engagements
- Vendor and Business Partner Risks
- Responsibility and Accountability for Managing Vendors and Business Partners.
- Communication Protocols for Vendors and Business Partners.
- Exception Handling Procedures from Vendors and Business Partners.
- Vendor and Business Partner Performance.
- Procedures for Addressing Issues Identified During Vendor and Business Partner Assessments.
- Procedures for Terminating Vendor and Business Partner Relationships.
- Process to obtains Confidentiality Commitments from Vendors and Business Partners.
- Assessment process for Compliance with Confidentiality Commitments of Vendors and Business Partners.
- Process to obtains Privacy Commitments from Vendors and Business Partners.
- Assessment process for Compliance with Privacy Commitments of Vendors and Business Partners.
Each of these operational processes are part of the implementation of a third-party risk management program structure. However, to make the controls auditable and testable will require not only compliance documentation but artifacts and testing of the controls, to provide evidence to auditors of the implementation of the third -party governance program requirements. Multiple regulatory drivers are triggering changes to mature the third- party risk governance process. Creating an external assurance maturity calendar, requires taking a long view, embedding into readiness this year for what is tested next year.
Business Readiness
While it can be easy to feel like throwing in the towel, the reality is the SOC boxing matches will continue, and evolve as new scoring mechanisms are defined. Here are six readiness steps to tackle, one per month to avoid feeling on the ropes or down for the count while you prepare for an audit of your third-party risk governance program.
-
-
- Policies: Review and create a comparison of the Vendor and Risk Management criteria to your Third-Party Policies and Procedures. Plan for need for additional compliance documentation, process maps.
- Employee Knowledge: Prepare employees who manage controls, by sending out a self-assessment of their understanding of the roles, accountabilities and governance for third party risk. Update control owners, assess internal expertise and identify gaps.
- Technology: Conduct an assessment with your current GRC tools to prepare for any IT or configuration changes.
- Benchmark: Refresh benchmarking the maturity of your Third-Party Program to the Vendor Risk Management Maturity Model
- Risk Reporting: Review existing scorecards, dashboards and management reporting on third party risk governance and identify changes to meet the new common criteria.
- Process Refinement: Embed security, confidentiality, and privacy commitment processes into a common third party continuous monitoring process.
-
Yes, audit standard changes can feel daunting, and complex. However, just like there are weight levels in boxing to make the fights fair, assessing a third-party program is also risk based. Focus on the critical activities, critical services, critical controls, and third-party relationships, most of these requirements are not dramatically new, they are simply driving maturity into the third-party risk governance program that have been in place for financial controls.
Linnea Solem is a former Shared Assessments Program Steering Committee Chairperson, and current Advisory Board Member. She is the President and Founder of Solem Risk Partners, LLC a management consulting and advisory services company focused on Third Party Risk Governance, Privacy Program Management, and Enterprise Risk Management.

