Third Party IoT Security: Interpreting Survey Results in the Context of a Shifting Security Paradigm

Shared Assessment’s just published Ponemon research report The Internet of Things (IoT): A new Era of Third Party Risk provides a great snapshot of current IoT Risk management both within an organization’s four walls and with the third parties that so often support mission critical activities.
Many of the report’s findings are troublesome: the lack of Board understanding about IoT in the context of both in-house and third party risk management; the lack of an integrated approach to IoT risk management; even the lack of some of the most basic elements required to build an effective IoT risk management program, such as having a complete inventory of IoT devices (only 16% of respondents said they had such an inventory). Those findings come despite the recognition that security incidents related to IoT devices or applications could be catastrophic (94% of survey respondents said they thought such a result could emerge within two years).
What are the consequences of such a large gap between recognized IoT risks and an ability to effectively mitigate them? What are the key steps required to close that gap?
Last October’s headline making IoT-based DDoS attack was a small sample of what the future may hold. That attack disrupted a number of websites including Twitter, Netflix, PayPal, Verizon and Comcast, and was orchestrated by the Mirai botnet. That botnet employed “tens of millions” of malware-infected devices connected to the internet (Bloomberg, October 21, 2016).
The Internet of Things report’s key findings provide important insight on how the state of IoT security will play into the evolving threat landscape as the number of IoT devices expands over the next few years.
The Internet of Things results are strongly indicative of a low level of IoT risk management maturity: only 30% of respondents reported that managing third party IoT risks is an organizational priority; only 27% of respondents said their organization allocates sufficient resources to manage third party IoT risks; and only 25% reported that their governing board required assurances that third party IoT risk was being assessed, managed and monitored appropriately. Only 31% of organizations regularly report to the CEO and board on the effectiveness of their third party risk management program. Why?
More than half of respondents said the effectiveness of their organization’s third party risk management program was not a priority for the board and CEO. Perhaps even more disturbing is the perception (by 56% of respondents) that it is not possible to determine whether third party safeguards and IoT security policies are sufficient to prevent a data breach. This last finding suggests that many respondents don’t understand what a mature IoT risk management environment would comprise.
The sheer magnitude in the expected growth of IoT devices suggests that a high degree of automation is vital to effective IoT risk management. Industrial firms have had a focus on Operational Technology (OT) for years because of its essential nature in the production process. What is OT? Gartner defines operational technology as “hardware and software that detects or causes a change through the direct monitoring and/or control of physical devices, processes and events in the enterprise.”
For those outside of organizations where industrial device control has been a longstanding requirement, the importance of operational technology security may not be second hand. That will change as IoT security concerns emerge, and we’ll rapidly see a security environment where information security, IT security, OT security and physical security require close coordination to achieve effective risk mitigation. One key question is how quickly that convergence will occur, and there is ample evidence to suggest that here too we’re early-on in that maturity process.
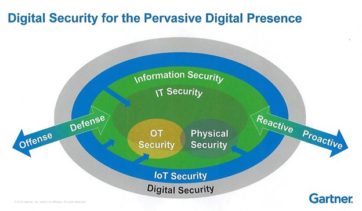
Source: Gartner, 2015
No matter how the IoT security ecosystem evolves, there are steps organizations can take now to protect against emerging IoT threats. The most important are these:
- Ensure that third-party and IoT risk management processes are defined and operational at all governance levels, up to and including the board.
- Update asset management processes and inventory systems to include IoT devices, and understand the security characteristics of all inventoried devices. When devices are found to have inadequate security controls, replace them.
- Enhance third party contracts and polices to include IoT specific requirements.
- Expand third party assessment techniques and processes to ensure the presence and effectiveness of controls specific to IoT devices.
- Develop specific sourcing and procurement requirements to ensure that only IoT devices designed with appropriate security functions included and enabled are considered for product selection and acquisition.
For more than four decades, Gary Roboff, Senior Advisor, The Santa Fe Group,, contributed his outstanding talents to the in financial services planning and management, including 25 years at JP Morgan Chase where he retired as Senior Vice President of Electronic Commerce. Gary has worked extensively in electronic payments, payments fraud, third part risk management, privacy and information utilization, as well as business frameworks and standards for electronic commerce applications.
