Data Privacy Roadmap: Where We Are, Where We’re Headed, How We Can Get There

Since the introduction of the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA), data privacy has become an essential aspect of Third Party Risk Management (TPRM). With constant changes in data privacy regulations, staying up-to-date with international and state-specific rules is crucial to ensure compliance.
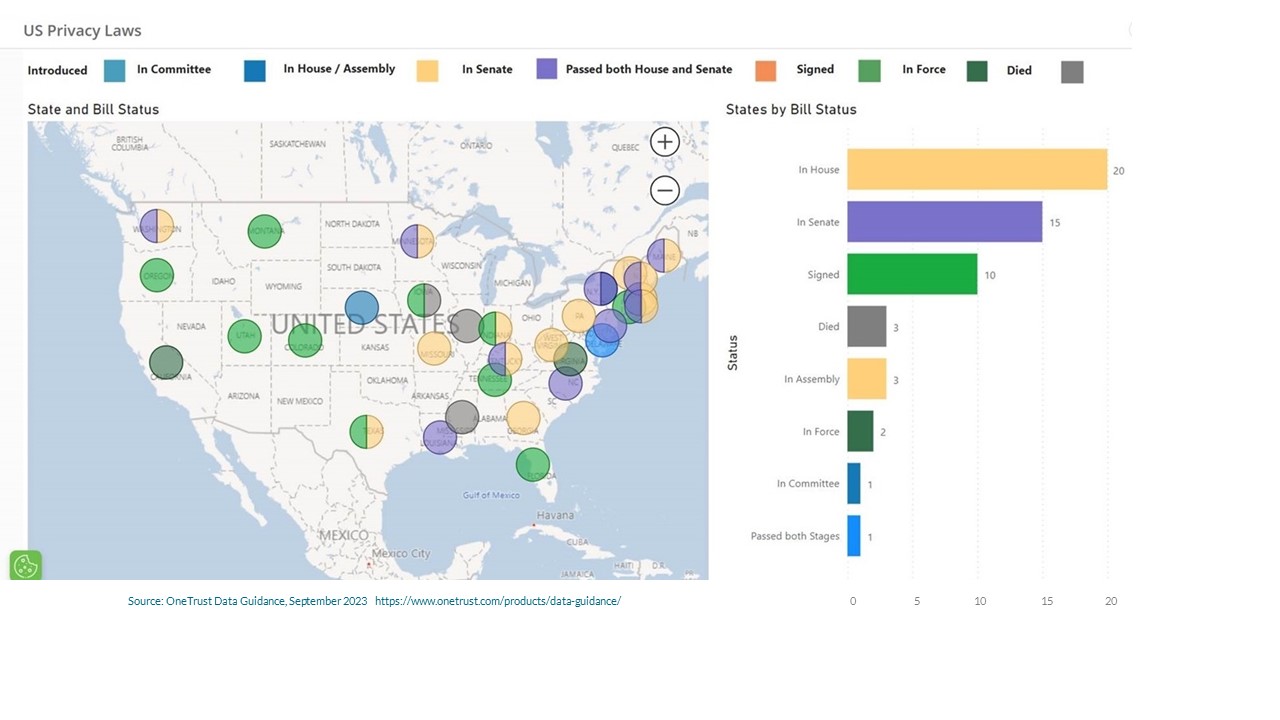
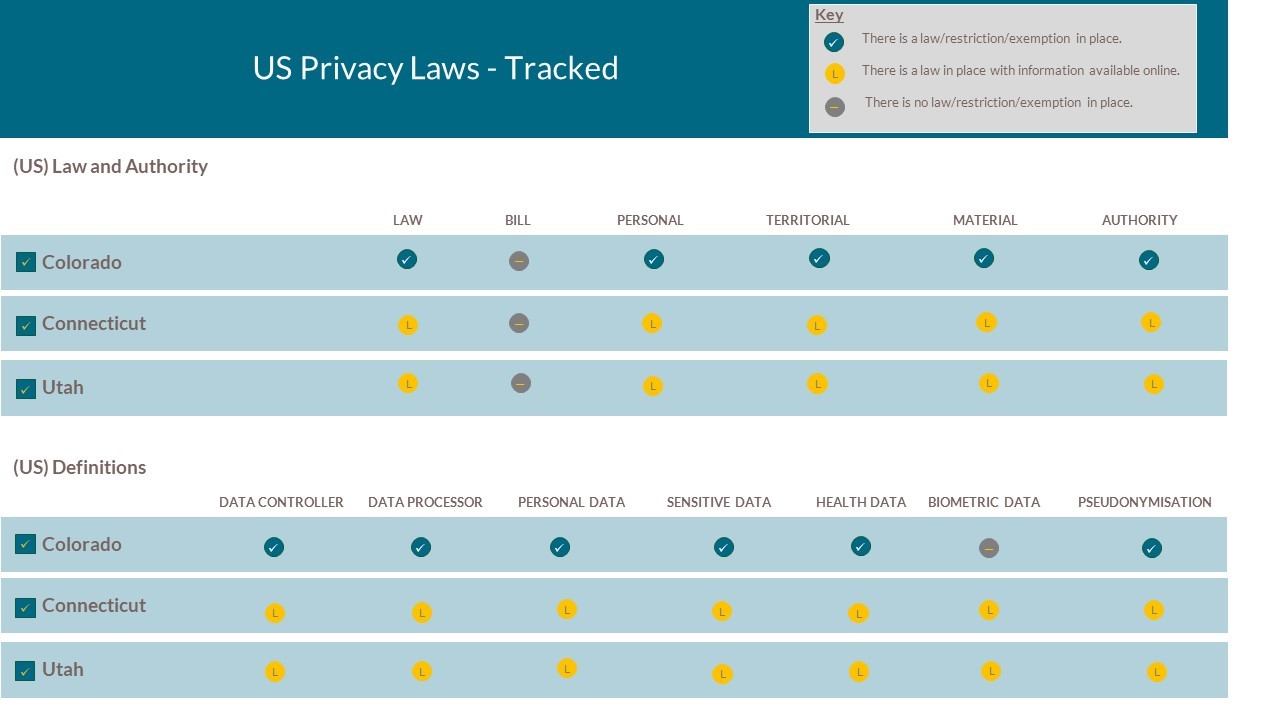
The absence of consistent national regulation is made even more complex by the additional provisions that different state lawmakers add to privacy rules. These rules often have conflicting information on both the level of protection required and what is covered by the rules. This includes measures such as securing data collectors for payment cards, using encryption, disclosing breaches and the methods used for disclosure, records retention and destruction, and, in the case of the Nevada Security and Privacy of
Personal Information regulations, violations of the rules being deemed as deceptive trade practices, which was added to the original 2004 rule in 2021.
To make their data governance processes more robust, TPRM programs should:
- Start with sound models: The Massachusetts Standards for the Protections of Personal Information of Residents of the Commonwealth stands out as a model that affords a starting template for practitioners. Meet or exceed NIST 800-161 Rev 1. Cybersecurity Supply Chain Risk Management Practices the oversight guidance by CISO (“or equivalent”) to ensure access rights to privacy data are tracked through third and Nth parties. Using a comprehensive model provides a defensible stance.
- Set and Enforce Processing Data Privacy Rights Requests: Know where your personal data is on premise; in your managed clouds; and at your vendors to ensure robust controls around the processing of requests, including controls around mechanisms for terminating access to data whenever needed.
- Know the rules: And follow them. If violations occur, know your rights. Many jurisdictions have no-fault timelines for resolving issues. When remediating, meet timelines and provide accurate reporting of changes made to mitigate identified issues.
- Think ROPA: Outside the US, Record of Processing Activities (ROPA) documents ingress/egress of data sets that third parties touch. Adopting a ROPA-like approach, where the data goes, who handles that information, and the format (de-identified, tokenized, etc.) is consistently documented and monitored, provides a higher level of data governance.
- Use contracting and monitoring effectively: Contractually require third parties to verify where data resides and chain of custody requirements. Specifically, it requires notification of Nth touching data sets with the right to refuse that permission and that Nth parties must meet or exceed agreed-upon controls.
- Implement enterprise policies: To enhance efficiency and effectiveness, it is essential to ensure that enterprise policies are being implemented. Rules that are not being put into operation cannot produce sound outcomes, and thus, it is necessary to evaluate and improve the policies. Additionally, it is crucial to enhance consent management at the portal level. In doing so, it is essential to differentiate which data is under the control of the outsourcer and which data remains under the service provider’s or data processor’s control. This differentiation is a significant step in assessing the risk involved in data-sharing relationships. To mitigate risks, it is recommended to include clawback provisions such as encryption and/or tokenization. These provisions should also cover timely notification of breaches, hold harmless clauses, and specific audit/monitoring rights.
For Shared Assessments members who are product users:
- Incorporating the Shared Assessments Data Governance Products into data privacy assessments provides insight into data governance processes and possible compliance gaps. The type of tracking and analysis available helps practitioners to stay abreast of such changes as the 2023 SEC expansion of the right to audit rules governing privacy right searches, reflecting the growing mandate to go beyond the control testing ‘light touch’ that we have seen before this shift in the data privacy landscape. With data/screenshots mandated as documentation for assessments and monitoring, the Data Governance Products provide a tracking mechanism for information tied to PII and other data that may fall under the various rules globally.
- Scoping the Privacy Sections of the Standardized Information Gathering (SIG) Questionnaire and the Standardized Control Assessment (SCA) by using questions related to CCPA and other state regulatory privacy obligations.
In this ever-changing environment, there is a chance to succeed or fail. Your information security programs may not require much change if they are already strong. However, it’s advisable to review them proactively to improve protection levels and make updates as needed in response to changes as they occur. You should also frequently audit third-party security practices and maintain an inventory of all the entities with data access. It’s essential to thoroughly review emerging technologies that third parties are using and consider adopting them before implementation.
To ensure the most accessible compliance pathway, consider setting the most restrictive regulation applicable to your setting as a default for all your data management processes. This approach demands privacy by design in all products and services. To achieve this, liaise with all cost centers and enlist the support of senior leadership to prioritize data security efforts across the enterprise. While privacy-by-design may be initially more expensive, it will prove to be a competitive advantage as the landscape evolves.
Additional Resources from Shared Assessments:
- Data Privacy Day 2021
- AI Risk and Data Governance
- Data Retention
- Transatlantic Data Flows
- Data Privacy Day 2019
- Data Privacy Implications For TPRM
- 2023 TPRM Product Suite
State-by-State Privacy Rules and Other Related Resources:
- California Consumer Privacy Act
- Colorado Privacy Act
- Massachusetts Standards for the Protections of Personal Information of Residents of the Commonwealth
- Nevada Security and Privacy of Personal Information
- Utah Consumer Privacy Act
- CFPB Article: CFPB Takes Action Against Bank of America for Illegally Charging Junk Fees, Withholding Credit Card Rewards, and Opening Fake Accounts.
- Guidance on the Ethical Development and Use of Artificial Intelligence
- Biden-Harris Administration Announces Cybersecurity Labeling Program for Smart Devices to Protect American Consumers
- Post-Quantum Cryptography (PQC) Digital Signature Schemes; NIST Announces Additional Digital Signature Candidates for the PQC Standardization Process · Ethical AI; Office of the Privacy Commissioner for Personal Data, Hong Kong
- FTC Seeks Comment on New Parental Consent Mechanism Under COPPA
- Shaping Trust in the Age of AI, Jim Routh
- You can join committees at NIST (through their website – search “join” and select those committees that are of interest to follow).



